[index] AT-AR2010V コマンドリファレンス 5.4.9

(本社) |
(支社) |
|
| WAN側物理インターフェース | eth1 | eth1 |
| WAN側(eth1)IPv6アドレス | 自動設定(SLAAC) | 自動設定(SLAAC) |
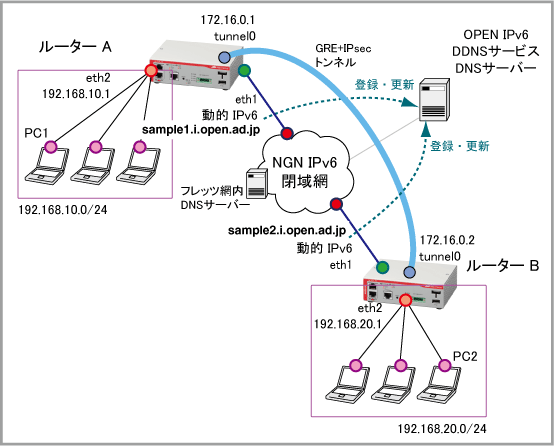
| LAN側(eth2)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 |
| IKEバージョン | ||
| ローカルID | sample1.i.open.ad.jp | sample2.i.open.ad.jp |
| リモートID | sample2.i.open.ad.jp | sample1.i.open.ad.jp |
| 専用更新ホスト名* | update-0123456789abcdefff.i.open.ad.jp | update-fffedcba9876543210.i.open.ad.jp |
| ホスト名(FQDN) | sample1.i.open.ad.jp | sample2.i.open.ad.jp |
| * ルーターが取得したIPv6アドレスを「OPEN IPv6 ダイナミック DNS for フレッツ・光ネクスト」サービスに登録したホスト名(FQDN)と関連付けるには、「専用更新ホスト名」を使用します。 * ルーターが使用するホスト名(FQDN)や専用更新ホスト名は、あらかじめ取得してあるものとします。 |
||
interface eth1 ipv6 enable
interface eth2 ip address 192.168.10.1/24
ipv6 forwarding
zone private_ipv4 network lan ip subnet 172.16.0.0/30 ip subnet 192.168.0.0/16
zone external_ipv6 network wan ipv6 subnet ::/0 interface eth1 host eth1 ipv6 address dynamic interface eth1
application dhcpv6 protocol udp dport 546 to 547
application esp protocol 50
application gre protocol 47
application icmpv6 protocol ipv6-icmp
application isakmp protocol udp dport 500
firewall rule 10 permit any from external_ipv6.wan.eth1 to external_ipv6 rule 20 permit isakmp from external_ipv6 to external_ipv6.wan.eth1 rule 30 permit esp from external_ipv6 to external_ipv6.wan.eth1 rule 40 permit gre from external_ipv6 to external_ipv6.wan.eth1 rule 50 permit dhcpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 60 permit icmpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 100 permit any from private_ipv4 to private_ipv4 protect
crypto isakmp key secret hostname sample2.i.open.ad.jp
interface tunnel0 tunnel source eth1 tunnel destination sample2.i.open.ad.jp tunnel local name sample1.i.open.ad.jp tunnel remote name sample2.i.open.ad.jp tunnel protection ipsec tunnel mode gre ipv6 ip address 172.16.0.1/30 ip tcp adjust-mss 1366
ping-poll 1 ip 172.16.0.2 up-count 3 fail-count 3 sample-size 3 active
trigger 1 type periodic 1 script 1 open_ddns.scp trigger 10 type ping-poll 1 down script 1 periodic-update.scp trigger 11 type ping-poll 1 up script 1 periodic-update-delete.scp
ip route 192.168.20.0/24 tunnel0
end
interface eth1 ipv6 enable
interface eth2 ip address 192.168.20.2/24
ipv6 forwarding
zone private_ipv4 network lan ip subnet 172.16.0.0/24 ip subnet 192.168.0.0/16
zone external_ipv6 network wan ipv6 subnet ::/0 interface eth1 host eth1 ipv6 address dynamic interface eth1
application dhcpv6 protocol udp dport 546 to 547
application esp protocol 50
application gre protocol 47
application icmpv6 protocol ipv6-icmp
application isakmp protocol udp dport 500
firewall rule 10 permit any from external_ipv6.wan.eth1 to external_ipv6 rule 20 permit isakmp from external_ipv6 to external_ipv6.wan.eth1 rule 30 permit esp from external_ipv6 to external_ipv6.wan.eth1 rule 40 permit gre from external_ipv6 to external_ipv6.wan.eth1 rule 50 permit dhcpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 60 permit icmpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 100 permit any from private_ipv4 to private_ipv4 protect
crypto isakmp key secret hostname sample1.i.open.ad.jp
interface tunnel0 tunnel source eth1 tunnel destination sample1.i.open.ad.jp tunnel local name sample2.i.open.ad.jp tunnel remote name sample1.i.open.ad.jp tunnel protection ipsec tunnel mode gre ipv6 ip address 172.16.0.2/30 ip tcp adjust-mss 1366
ping-poll 1 ip 172.16.0.1 up-count 3 fail-count 3 sample-size 3 active
trigger 1 type periodic 1 script 1 open_ddns.scp trigger 10 type ping-poll 1 down script 1 periodic-update.scp trigger 11 type ping-poll 1 up script 1 periodic-update-delete.scp
ip route 192.168.10.0/24 tunnel0
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility kern msgtext Firewall ↓
awplus# show log | include Firewall ↓
! interface eth1 ipv6 enable ! interface eth2 ip address 192.168.10.1/24 ! ipv6 forwarding ! zone private_ipv4 network lan ip subnet 172.16.0.0/30 ip subnet 192.168.0.0/16 ! zone external_ipv6 network wan ipv6 subnet ::/0 interface eth1 host eth1 ipv6 address dynamic interface eth1 ! application dhcpv6 protocol udp dport 546 to 547 ! application esp protocol 50 ! application gre protocol 47 ! application icmpv6 protocol ipv6-icmp ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from external_ipv6.wan.eth1 to external_ipv6 rule 20 permit isakmp from external_ipv6 to external_ipv6.wan.eth1 rule 30 permit esp from external_ipv6 to external_ipv6.wan.eth1 rule 40 permit gre from external_ipv6 to external_ipv6.wan.eth1 rule 50 permit dhcpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 60 permit icmpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 100 permit any from private_ipv4 to private_ipv4 protect ! crypto isakmp key secret hostname sample2.i.open.ad.jp ! interface tunnel0 tunnel source eth1 tunnel destination sample2.i.open.ad.jp tunnel local name sample1.i.open.ad.jp tunnel remote name sample2.i.open.ad.jp tunnel protection ipsec tunnel mode gre ipv6 ip address 172.16.0.1/30 ip tcp adjust-mss 1366 ! ping-poll 1 ip 172.16.0.2 up-count 3 fail-count 3 sample-size 3 active ! trigger 1 type periodic 1 script 1 open_ddns.scp trigger 10 type ping-poll 1 down script 1 periodic-update.scp trigger 11 type ping-poll 1 up script 1 periodic-update-delete.scp ! ip route 192.168.20.0/24 tunnel0 ! end
! interface eth1 ipv6 enable ! interface eth2 ip address 192.168.20.2/24 ! ipv6 forwarding ! zone private_ipv4 network lan ip subnet 172.16.0.0/24 ip subnet 192.168.0.0/16 ! zone external_ipv6 network wan ipv6 subnet ::/0 interface eth1 host eth1 ipv6 address dynamic interface eth1 ! application dhcpv6 protocol udp dport 546 to 547 ! application esp protocol 50 ! application gre protocol 47 ! application icmpv6 protocol ipv6-icmp ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from external_ipv6.wan.eth1 to external_ipv6 rule 20 permit isakmp from external_ipv6 to external_ipv6.wan.eth1 rule 30 permit esp from external_ipv6 to external_ipv6.wan.eth1 rule 40 permit gre from external_ipv6 to external_ipv6.wan.eth1 rule 50 permit dhcpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 60 permit icmpv6 from external_ipv6 to external_ipv6.wan.eth1 rule 100 permit any from private_ipv4 to private_ipv4 protect ! crypto isakmp key secret hostname sample1.i.open.ad.jp ! interface tunnel0 tunnel source eth1 tunnel destination sample1.i.open.ad.jp tunnel local name sample2.i.open.ad.jp tunnel remote name sample1.i.open.ad.jp tunnel protection ipsec tunnel mode gre ipv6 ip address 172.16.0.2/30 ip tcp adjust-mss 1366 ! ping-poll 1 ip 172.16.0.1 up-count 3 fail-count 3 sample-size 3 active ! trigger 1 type periodic 1 script 1 open_ddns.scp trigger 10 type ping-poll 1 down script 1 periodic-update.scp trigger 11 type ping-poll 1 up script 1 periodic-update-delete.scp ! ip route 192.168.10.0/24 tunnel0 ! end
enable ping ipv6 update-0123456789abcdefff.i.open.ad.jp repeat 2 exit
enable conf t trigger 20 type periodic 1 script 1 host-change.scp exit exit
enable conf t no trigger 20 exit
enable clear isakmp sa force conf t int tunnel0 tunnel dest sample2.i.open.ad.jp exit exit
enable ping ipv6 update-fffedcba9876543210.i.open.ad.jp repeat 2 exit
enable conf t trigger 20 type periodic 1 script 1 host-change.scp exit exit
enable conf t no trigger 20 exit
enable clear isakmp sa force conf t int tunnel0 tunnel dest sample1.i.open.ad.jp exit exit
(C) 2016 - 2019 アライドテレシスホールディングス株式会社
PN: 613-002311 Rev.R