[index] AT-AR2050V/AT-AR3050S/AT-AR4050S コマンドリファレンス 5.5.0

| 接続用ユーザー名 | user@ispA | user@ispB |
| 接続用パスワード | isppasswdA | isppasswdB |
| PPPoEサービス名 | 指定なし | 指定なし |
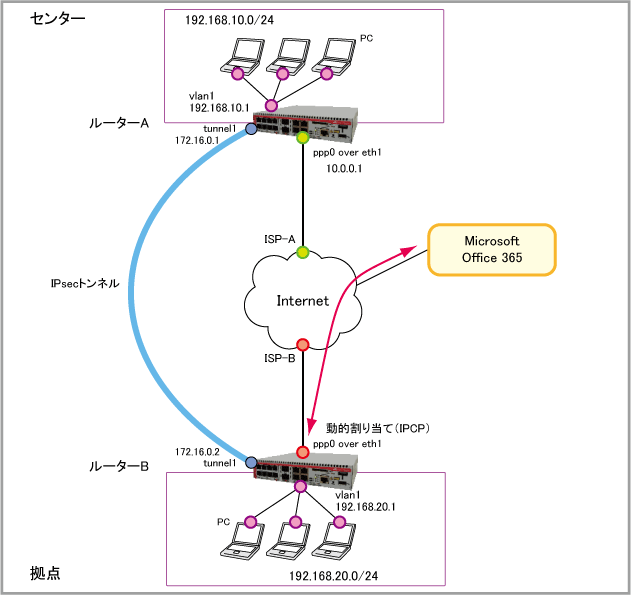
| WAN側IPアドレス | 10.0.0.1 | 動的割り当て(IPCP) |
| DNSサーバー | 自動取得(IPCP) | 自動取得(IPCP) |
| WAN側物理インターフェース | eth1 | eth1 |
| WAN側(ppp0)IPアドレス | 10.0.0.1/32 | 接続時にISPから取得 |
| LAN側(vlan1)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 |
| IPsecトンネル(tunnel1)IPアドレス | 172.16.0.1/30 | 172.16.0.2/30 |
no spanning-tree rstp enable
interface eth1 encapsulation ppp 0
interface ppp0 ppp ipcp dns request keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu
interface vlan1 ip address 192.168.10.1/24
zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private no-state-enforcement rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 rule 70 permit dns from public.wan.ppp0 to public.wan protect
nat rule 10 masq any from private to public enable
crypto isakmp key secret address RouterB
interface tunnel1 mtu 1300 tunnel source ppp0 tunnel destination dynamic tunnel remote name RouterB tunnel protection ipsec tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260
ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 tunnel1 ip route 192.168.20.0/24 Null 254
ip dns forwarding
end
no spanning-tree rstp enable
interface eth1 encapsulation ppp 0
interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@ispB ppp password isppasswdB ip tcp adjust-mss pmtu
interface vlan1 ip address 192.168.20.1/24
ips category http-events action deny protect
zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 network tunnel ip subnet 0.0.0.0/0 interface tunnel1
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 host office ip address dynamic fqdn www.office.com
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private no-state-enforcement rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 rule 70 permit dns from public.wan.ppp0 to public.wan protect
nat rule 10 masq any from private to public enable
crypto isakmp key secret address 10.0.0.1
policy-based-routing ip policy-route 10 from private to public.wan.office nexthop ppp0 policy-based-routing enable
tunnel security-reprocessing
interface tunnel1 mtu 1300 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name RouterB tunnel protection ipsec tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260
ip route 0.0.0.0/0 tunnel1 ip route 10.0.0.1/32 ppp0 ip route 192.168.10.0/24 tunnel1 ip route 192.168.10.0/24 Null 254
ip name-server 192.168.10.1 ip domain-lookup via-relay
ip dns forwarding ip dns forwarding cache size 1000
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility kern msgtext Firewall ↓
awplus# show log | include Firewall ↓
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.10.1/24 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private no-state-enforcement rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 rule 70 permit dns from public.wan.ppp0 to public.wan protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret address RouterB ! interface tunnel1 mtu 1300 tunnel source ppp0 tunnel destination dynamic tunnel remote name RouterB tunnel protection ipsec tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 tunnel1 ip route 192.168.20.0/24 Null 254 ! ip dns forwarding ! end
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@ispB ppp password isppasswdB ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.20.1/24 ! ips category http-events action deny protect ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 network tunnel ip subnet 0.0.0.0/0 interface tunnel1 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 host office ip address dynamic fqdn www.office.com ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private no-state-enforcement rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 rule 70 permit dns from public.wan.ppp0 to public.wan protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret address 10.0.0.1 ! policy-based-routing ip policy-route 10 from private to public.wan.office nexthop ppp0 policy-based-routing enable ! tunnel security-reprocessing ! interface tunnel1 mtu 1300 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name RouterB tunnel protection ipsec tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 ! ip route 0.0.0.0/0 tunnel1 ip route 10.0.0.1/32 ppp0 ip route 192.168.10.0/24 tunnel1 ip route 192.168.10.0/24 Null 254 ! ip name-server 192.168.10.1 ip domain-lookup via-relay ! ip dns forwarding ip dns forwarding cache size 1000 ! end
(C) 2015 - 2023 アライドテレシスホールディングス株式会社
PN: 613-003184 Rev.A