[index] AT-AR2050V/AT-AR3050S/AT-AR4050S コマンドリファレンス 5.5.1

| 接続先 | ||
| ブロードキャスト | ||
| リンク層アドレス(ARP)解決 | ||
| 経路設定時のネクストホップ指定方法 |
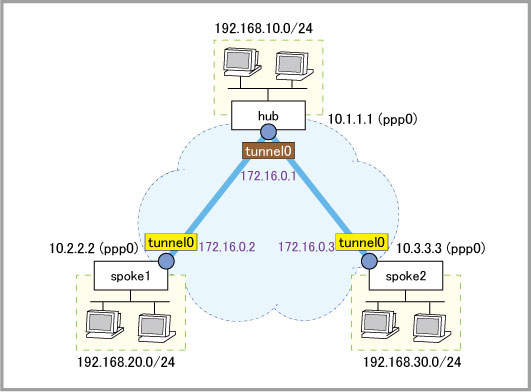
crypto isakmp key friend hostname hub interface tunnel0 tunnel mode gre multipoint tunnel source ppp0 tunnel endpoint dynamic tunnel local name hub tunnel protection ipsec ip address 172.16.0.1/28 ! ip route 192.168.20.0/24 172.16.0.2 ip route 192.168.30.0/24 172.16.0.3
crypto isakmp key friend hostname hub interface tunnel0 tunnel mode gre tunnel source ppp0 tunnel destination 10.1.1.1 tunnel local name spoke1 tunnel remote name hub tunnel protection ipsec ip address 172.16.0.2/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.30.0/24 172.16.0.1
crypto isakmp key friend hostname hub interface tunnel0 tunnel mode gre tunnel source ppp0 tunnel destination 10.1.1.1 tunnel local name spoke2 tunnel remote name hub tunnel protection ipsec ip address 172.16.0.3/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.20.0/24 172.16.0.1

crypto isakmp key friend1 hostname spoke1 crypto isakmp key friend2 hostname spoke2 interface tunnel0 tunnel mode gre multipoint tunnel source ppp0 tunnel endpoint dynamic tunnel local name hub tunnel protection ipsec ip address 172.16.0.1/28 ! ip route 192.168.20.0/24 172.16.0.2 ip route 192.168.30.0/24 172.16.0.3
crypto isakmp key friend1 hostname hub interface tunnel0 tunnel mode gre tunnel source ppp0 tunnel destination 10.1.1.1 tunnel local name spoke1 tunnel remote name hub tunnel protection ipsec ip address 172.16.0.2/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.30.0/24 172.16.0.1
crypto isakmp key friend2 hostname hub interface tunnel0 tunnel mode gre tunnel source ppp0 tunnel destination 10.1.1.1 tunnel local name spoke2 tunnel remote name hub tunnel protection ipsec ip address 172.16.0.3/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.20.0/24 172.16.0.1
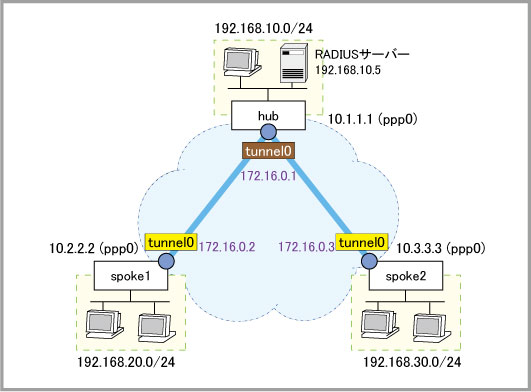
radius-server host 192.168.10.5 key RadiusPasswordHere aaa authentication isakmp default group radius crypto isakmp profile spoke remote authentication eap-radius transform 1 integrity SHA1 encryption AES128 group 14 crypto isakmp peer dynamic profile spoke crypto isakmp key friend hostname hub interface tunnel0 tunnel mode gre multipoint tunnel source ppp0 tunnel endpoint dynamic tunnel local name hub tunnel protection ipsec ip address 172.16.0.1/28 ! ip route 192.168.20.0/24 172.16.0.2 ip route 192.168.30.0/24 172.16.0.3
crypto isakmp profile hub local authentication eap-radius transform 1 integrity SHA1 encryption AES128 group 14 crypto isakmp peer hostname hub profile hub crypto isakmp key friend hostname hub crypto isakmp key friend1 hostname hub type eap interface tunnel0 tunnel mode gre tunnel source ppp0 tunnel destination 10.1.1.1 tunnel local name spoke1 tunnel remote name hub tunnel protection ipsec ip address 172.16.0.2/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.30.0/24 172.16.0.1
crypto isakmp profile hub local authentication eap-radius transform 1 integrity SHA1 encryption AES128 group 14 crypto isakmp peer hostname hub profile hub crypto isakmp key friend hostname hub crypto isakmp key friend2 hostname hub type eap interface tunnel0 tunnel mode gre tunnel source ppp0 tunnel destination 10.1.1.1 tunnel local name spoke2 tunnel remote name hub tunnel protection ipsec ip address 172.16.0.3/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.20.0/24 172.16.0.1
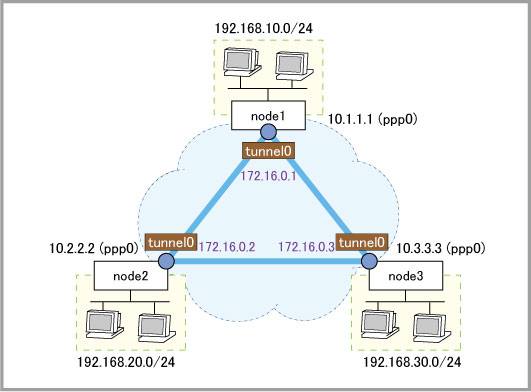
crypto isakmp key friend hostname node1 interface tunnel0 tunnel mode gre multipoint tunnel source ppp0 tunnel local name node1 tunnel endpoint 10.2.2.2 tunnel endpoint 10.3.3.3 tunnel protection ipsec ip address 172.16.0.1/28 ! ip route 192.168.20.0/24 172.16.0.2 ip route 192.168.30.0/24 172.16.0.3
crypto isakmp key friend hostname node2 interface tunnel0 tunnel mode gre multipoint tunnel source ppp0 tunnel local name node2 tunnel endpoint 10.1.1.1 tunnel endpoint 10.3.3.3 tunnel protection ipsec ip address 172.16.0.2/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.30.0/24 172.16.0.3
crypto isakmp key friend hostname node3 interface tunnel0 tunnel mode gre multipoint tunnel source ppp0 tunnel local name node3 tunnel endpoint 10.1.1.1 tunnel endpoint 10.2.2.2 tunnel protection ipsec ip address 172.16.0.3/28 ! ip route 192.168.10.0/24 172.16.0.1 ip route 192.168.20.0/24 172.16.0.2
awplus# show interface tunnel0 ↓ Interface tunnel0 Link is UP, administrative state is UP Hardware is Tunnel IPv4 address 172.16.0.1/28 broadcast 172.16.0.15 index 15 metric 1 mtu 1434 <UP,BROADCAST,RUNNING,MULTICAST> VRF Binding: Not bound SNMP link-status traps: Disabled Bandwidth 1g Tunnel source 10.1.1.1 Tunnel name local hub Tunnel protocol/transport gre multipoint, key disabled, sequencing disabled Tunnel endpoint 10.2.2.2 Tunnel endpoint 10.3.3.3 Tunnel TTL 64 Checksumming of packets disabled, path MTU discovery disabled Tunnel protection via IPsec (profile "default") Router Advertisement is disabled Router Advertisement default routes are accepted Router Advertisement prefix info is accepted input packets 56, bytes 3804, dropped 0, multicast packets 0 output packets 121, bytes 5364, multicast packets 0, broadcast packets 0 input average rate : 30 seconds 0 bps, 5 minutes 0 bps output average rate: 30 seconds 0 bps, 5 minutes 0 bps input peak rate 972 bps at 2019/03/14 00:30:13 output peak rate 1.53 Kbps at 2019/03/14 00:30:13 Time since last state change: 0 days 02:18:50
awplus# show arp ↓ IP Address LL Address Interface Port Type 172.16.0.2 10.2.2.2 tunnel0 - dynamic
awplus# show ipsec peer ↓ IPsec Selectors (local:remote) Address: 10.1.1.1 : any Protocol: gre:gre Port: any:any Mark: any:any Profile: default SPI (In:Out): c11b381d:cdfcfc96 Selectors: 10.1.1.1/32[gre] 10.2.2.2/32[gre] Proto: ESP Mode: transport Encryption: AES256 Integrity: SHA256 Expires: 28794s ISAKMP LocalID: hub RemoteID: spoke1 Cookies (Initiator:Responder) d67d8e23b5626547:cadf02b393a4047c Ver: 2 Lifetime: 84450s State: Established Authentication: PSK Group: 14 Encryption: AES256 NATT: no Integrity: SHA256 DPD: yes
(C) 2015 - 2021 アライドテレシスホールディングス株式会社
PN: 613-002107 Rev.AP