[index] AT-TQRシリーズ コマンドリファレンス 5.5.3

| ISP接続用ユーザー名 | user@ispA | user@ispB | user@ispC |
| ISP接続用パスワード | isppasswdA | isppasswdB | isppasswdC |
| PPPoEサービス名 | 指定なし | 指定なし | 指定なし |
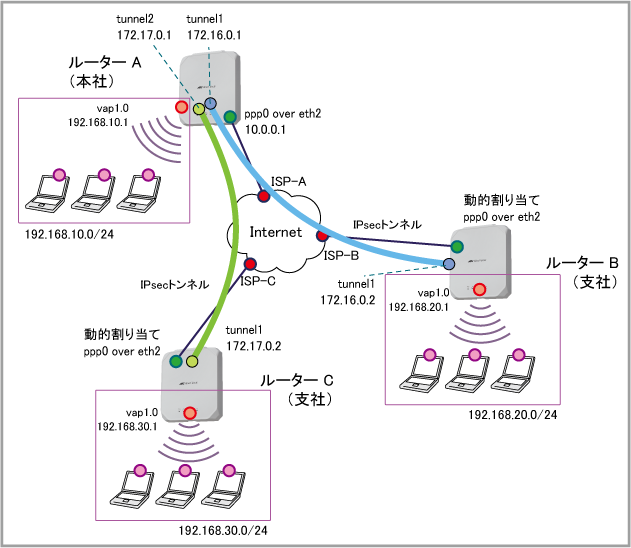
| WAN側IPアドレス | 10.0.0.1/32 | 動的割り当て(IPCP) | 動的割り当て(IPCP) |
| 接続形態 | 端末型(アドレス1個固定) | 端末型(アドレス1個不定) | 端末型(アドレス1個不定) |
| WAN側物理インターフェース | eth2 | eth2 | eth2 |
| WAN側(ppp0)IPアドレス | 10.0.0.1/32 | 接続時にISPから取得 | 接続時にISPから取得 |
| LAN側(vap1.0)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 | 192.168.30.1/24 |
| IKEバージョン・交換モード | |||
| アルゴリズム | |||
| ローカルID | 始点アドレス(デフォルト) | client_B | client_C |
| アルゴリズム | |||
awplus(config)# wireless ↓ awplus(config-wireless)# ap-profile local ↓ awplus(config-wireless-ap-prof)# radio 1 ↓ awplus(config-wireless-ap-prof-radio)# enable ↓ awplus(config-wireless-ap-prof-radio)# end ↓
awplus# wireless ap-configuration apply ap local ↓
Note本設定例では、ルーターとしての全体的な設定を示すため、無線機能に関してはデフォルト設定を利用した最小限の設定のみを示しています。
実際の運用にあたっては、「無線機能」章にある設定のポイントなどをご参照の上、SSID、セキュリティーなど要件にあわせた適切な設定を行ってから本手順(無線設定の適用)を実行してください。
wireless network 1 ssid allied24 network 17 ssid allied5-1 ap-profile local radio 1 enable vap 0 network 1 radio 2 vap 0 network 17 ap local
interface eth2 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu
interface vap1.0 ip address 192.168.10.1/24
zone private network lan ip subnet 172.16.0.0/30 ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 ip subnet 192.168.30.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret-ab hostname Client_B crypto isakmp key secret-ac hostname Client_C
crypto isakmp peer dynamic profile isakmp1
interface tunnel1 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 mtu 1300
interface tunnel2 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.1/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 tunnel1 ip route 192.168.20.0/24 Null 254 ip route 192.168.30.0/24 tunnel2 ip route 192.168.30.0/24 Null 254
log buffered level informational
end
interface eth2 encapsulation ppp 0
interface ppp0 keepalive ip address negotiated ppp username user@ispB ppp password isppasswdB ip tcp adjust-mss pmtu
interface vap1.0 ip address 192.168.20.1/24
zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret-ab address 10.0.0.1
crypto isakmp peer address 10.0.0.1 profile isakmp1
interface tunnel1 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel1 ip route 192.168.10.0/24 Null 254
log buffered level informational
end
interface eth2 encapsulation ppp 0
interface ppp0 keepalive ip address negotiated ppp username user@ispC ppp password isppasswdC ip tcp adjust-mss pmtu
interface vap1.0 ip address 192.168.30.1/24
zone private network lan ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.30.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 transform 2 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret-ac address 10.0.0.1
crypto isakmp peer address 10.0.0.1 profile isakmp1
interface tunnel1 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.2/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel1 ip route 192.168.10.0/24 Null 254
log buffered level informational
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility local5 ↓
awplus# show log | include Firewall ↓
! interface eth2 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu ! interface vap1.0 ip address 192.168.10.1/24 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 ip subnet 192.168.30.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret-ab hostname Client_B crypto isakmp key secret-ac hostname Client_C ! crypto isakmp peer dynamic profile isakmp1 ! interface tunnel1 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 mtu 1300 ! interface tunnel2 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.1/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 tunnel1 ip route 192.168.20.0/24 Null 254 ip route 192.168.30.0/24 tunnel2 ip route 192.168.30.0/24 Null 254 ! log buffered level informational ! end
! interface eth2 encapsulation ppp 0 ! interface ppp0 keepalive ip address negotiated ppp username user@ispB ppp password isppasswdB ip tcp adjust-mss pmtu ! interface vap1.0 ip address 192.168.20.1/24 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret-ab address 10.0.0.1 ! crypto isakmp peer address 10.0.0.1 profile isakmp1 ! interface tunnel1 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel1 ip route 192.168.10.0/24 Null 254 ! log buffered level informational ! end
! interface eth2 encapsulation ppp 0 ! interface ppp0 keepalive ip address negotiated ppp username user@ispC ppp password isppasswdC ip tcp adjust-mss pmtu ! interface vap1.0 ip address 192.168.30.1/24 ! zone private network lan ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.30.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 transform 2 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret-ac address 10.0.0.1 ! crypto isakmp peer address 10.0.0.1 profile isakmp1 ! interface tunnel1 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.2/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel1 ip route 192.168.10.0/24 Null 254 ! log buffered level informational ! end
(C) 2023 アライドテレシスホールディングス株式会社
PN: 613-003212 Rev.B