[index] AT-AR4000S-Cloud リファレンスマニュアル 5.5.4
Note本ページで述べるリンクアグリゲーションはリンク監視グループ内の良(good)回線間で負荷分散を行う機能であり、複数のスイッチポートを束ねるリンクアグリゲーション(IEEE 802.3ad)(ポートトランキング)とは異なります。

(本製品) |
(AR4050S) |
|
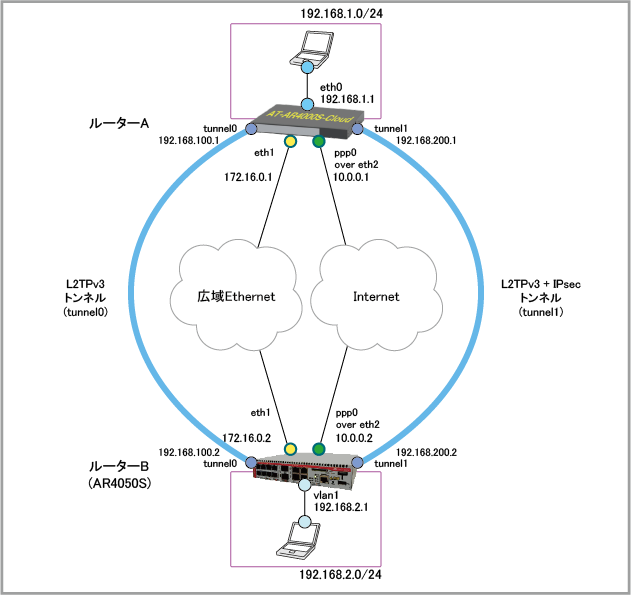
| 接続用ユーザー名 | user@ispA | user@ispB |
| 接続用パスワード | isppasswdA | isppasswdB |
| PPPoEサービス名 | 指定なし | 指定なし |
| WAN側IPアドレス | 10.0.0.1 | 10.0.0.2 |
| WAN側物理インターフェース(1)(広域Ethernet) | eth1 | eth1 |
| WAN側物理インターフェース(2)(インターネット) | eth2 | eth2 |
| WAN側IPアドレス(1) | 172.16.0.1/24 (eth1) | 172.16.0.2/24 (eth1) |
| WAN側IPアドレス(2) | 10.0.0.1/32 (ppp0) | 10.0.0.2/32 (ppp0) |
| LAN側IPアドレス | 192.168.1.1/24 (eth0) | 192.168.2.1/24 (vlan1) |
| L2TPv3トンネルIPアドレス(1) | 192.168.100.1/30 (tunnel0) | 192.168.100.2/30 (tunnel0) |
| L2TPv3トンネルIPアドレス(2) | 192.168.200.1/30 (tunnel1) | 192.168.200.2/30 (tunnel1) |
| eth0 | 192.168.1.1/24 | 管理用IPアドレス |
| eth1 | 未設定 | |
| eth2 | 未設定 |
Note構成が異なる場合はインターフェース名などを適宜読み替えてください。
interface eth1 ip address 172.16.0.1/24
interface eth2 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu
interface eth0 ip address 192.168.1.1/24
zone private network lan ip subnet 192.168.1.0/24 network peer ip subnet 192.168.2.0/24 network tunnel ip subnet 192.168.100.0/30 ip subnet 192.168.200.0/30 network wae ip subnet 172.16.0.0/24
zone public network eth2 ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1
application esp protocol 50
application isakmp protocol udp sport 500 dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.eth2.ppp0 to public.eth2 rule 40 permit isakmp from public.eth2 to public.eth2.ppp0 rule 50 permit esp from public.eth2.ppp0 to public.eth2 rule 60 permit esp from public.eth2 to public.eth2.ppp0 rule 70 permit l2tp from public.eth2.ppp0 to public.eth2 rule 80 permit l2tp from public.eth2 to public.eth2.ppp0 protect
nat rule 10 masq any from private to public enable
ips category http-events action deny protect
crypto isakmp key secret address 10.0.0.2
linkmon probe name PROBE0 type icmp-ping destination 192.168.100.2 egress interface tunnel0 source 192.168.100.1 interval 1000 enable
linkmon probe name PROBE1 type icmp-ping destination 192.168.200.2 egress interface tunnel1 source 192.168.200.1 interval 1000 enable
linkmon group tunnelgroup member 10 destination 192.168.100.2 probe PROBE0 member 20 destination 192.168.200.2 probe PROBE1 load-balancing
linkmon profile tunnelquality consecutive-probe-loss bad-when 3 consecutive-probe-loss good-when 2 consecutive-probe-loss unreachable-when 10
policy-based-routing ip policy-route 10 from private.lan to private.peer linkmon-group tunnelgroup linkmon-profile tunnelquality policy-based-routing enable
interface tunnel0 mtu 1500 tunnel source eth1 tunnel destination 172.16.0.2 tunnel local id 1 tunnel remote id 2 tunnel mode l2tp v3 ip address 192.168.100.1/30
interface tunnel1 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.2 tunnel local id 3 tunnel remote id 4 tunnel protection ipsec tunnel mode l2tp v3 ip address 192.168.200.1/30
ip route 0.0.0.0/0 ppp0 ip route 192.168.2.0/24 192.168.100.2 ip route 192.168.2.0/24 192.168.200.2
end
no spanning-tree rstp enable
interface eth1 ip address 172.16.0.2/24
interface eth2 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispB ppp password isppasswdB ip address 10.0.0.2/32 ip tcp adjust-mss pmtu
interface vlan1 ip address 192.168.2.1/24
zone private network lan ip subnet 192.168.2.0/24 network peer ip subnet 192.168.1.0/24 network tunnel ip subnet 192.168.100.0/30 ip subnet 192.168.200.0/30 network wae ip subnet 172.16.0.0/24
zone public network eth2 ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.2
application esp protocol 50
application isakmp protocol udp sport 500 dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.eth2.ppp0 to public.eth2 rule 40 permit isakmp from public.eth2 to public.eth2.ppp0 rule 50 permit esp from public.eth2.ppp0 to public.eth2 rule 60 permit esp from public.eth2 to public.eth2.ppp0 rule 70 permit l2tp from public.eth2.ppp0 to public.eth2 rule 80 permit l2tp from public.eth2 to public.eth2.ppp0 protect
nat rule 10 masq any from private to public enable
ips category http-events action deny protect
crypto isakmp key secret address 10.0.0.1
linkmon probe name PROBE0 type icmp-ping destination 192.168.100.1 egress interface tunnel0 source 192.168.100.2 interval 1000 enable
linkmon probe name PROBE1 type icmp-ping destination 192.168.200.1 egress interface tunnel1 source 192.168.200.2 interval 1000 enable
linkmon group tunnelgroup member 10 destination 192.168.100.1 probe PROBE0 member 20 destination 192.168.200.1 probe PROBE1 load-balancing
linkmon profile tunnelquality consecutive-probe-loss bad-when 3 consecutive-probe-loss good-when 2 consecutive-probe-loss unreachable-when 10
policy-based-routing ip policy-route 10 from private.lan to private.peer linkmon-group tunnelgroup linkmon-profile tunnelquality policy-based-routing enable
interface tunnel0 mtu 1500 tunnel source eth1 tunnel destination 172.16.0.1 tunnel local id 2 tunnel remote id 1 tunnel mode l2tp v3 ip address 192.168.100.2/30
interface tunnel1 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local id 4 tunnel remote id 3 tunnel protection ipsec tunnel mode l2tp v3 ip address 192.168.200.2/30
ip route 0.0.0.0/0 ppp0 ip route 192.168.1.0/24 192.168.100.1 ip route 192.168.1.0/24 192.168.200.1
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility local5 ↓
awplus# show log | include Firewall ↓
! interface eth1 ip address 172.16.0.1/24 ! interface eth2 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu ! interface eth0 ip address 192.168.1.1/24 ! zone private network lan ip subnet 192.168.1.0/24 network peer ip subnet 192.168.2.0/24 network tunnel ip subnet 192.168.100.0/30 ip subnet 192.168.200.0/30 network wae ip subnet 172.16.0.0/24 ! zone public network eth2 ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.eth2.ppp0 to public.eth2 rule 40 permit isakmp from public.eth2 to public.eth2.ppp0 rule 50 permit esp from public.eth2.ppp0 to public.eth2 rule 60 permit esp from public.eth2 to public.eth2.ppp0 rule 70 permit l2tp from public.eth2.ppp0 to public.eth2 rule 80 permit l2tp from public.eth2 to public.eth2.ppp0 protect ! nat rule 10 masq any from private to public enable ! ips category http-events action deny protect ! crypto isakmp key secret address 10.0.0.2 ! linkmon probe name PROBE0 type icmp-ping destination 192.168.100.2 egress interface tunnel0 source 192.168.100.1 interval 1000 enable ! linkmon probe name PROBE1 type icmp-ping destination 192.168.200.2 egress interface tunnel1 source 192.168.200.1 interval 1000 enable ! linkmon group tunnelgroup member 10 destination 192.168.100.2 probe PROBE0 member 20 destination 192.168.200.2 probe PROBE1 load-balancing ! linkmon profile tunnelquality consecutive-probe-loss bad-when 3 consecutive-probe-loss good-when 2 consecutive-probe-loss unreachable-when 10 ! policy-based-routing ip policy-route 10 from private.lan to private.peer linkmon-group tunnelgroup linkmon-profile tunnelquality policy-based-routing enable ! interface tunnel0 mtu 1500 tunnel source eth1 tunnel destination 172.16.0.2 tunnel local id 1 tunnel remote id 2 tunnel mode l2tp v3 ip address 192.168.100.1/30 ! interface tunnel1 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.2 tunnel local id 3 tunnel remote id 4 tunnel protection ipsec tunnel mode l2tp v3 ip address 192.168.200.1/30 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.2.0/24 192.168.100.2 ip route 192.168.2.0/24 192.168.200.2 ! end
! no spanning-tree rstp enable ! interface eth1 ip address 172.16.0.2/24 ! interface eth2 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispB ppp password isppasswdB ip address 10.0.0.2/32 ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.2.1/24 ! zone private network lan ip subnet 192.168.2.0/24 network peer ip subnet 192.168.1.0/24 network tunnel ip subnet 192.168.100.0/30 ip subnet 192.168.200.0/30 network wae ip subnet 172.16.0.0/24 ! zone public network eth2 ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.2 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.eth2.ppp0 to public.eth2 rule 40 permit isakmp from public.eth2 to public.eth2.ppp0 rule 50 permit esp from public.eth2.ppp0 to public.eth2 rule 60 permit esp from public.eth2 to public.eth2.ppp0 rule 70 permit l2tp from public.eth2.ppp0 to public.eth2 rule 80 permit l2tp from public.eth2 to public.eth2.ppp0 protect ! nat rule 10 masq any from private to public enable ! ips category http-events action deny protect ! crypto isakmp key secret address 10.0.0.1 ! linkmon probe name PROBE0 type icmp-ping destination 192.168.100.1 egress interface tunnel0 source 192.168.100.2 interval 1000 enable ! linkmon probe name PROBE1 type icmp-ping destination 192.168.200.1 egress interface tunnel1 source 192.168.200.2 interval 1000 enable ! linkmon group tunnelgroup member 10 destination 192.168.100.1 probe PROBE0 member 20 destination 192.168.200.1 probe PROBE1 load-balancing ! linkmon profile tunnelquality consecutive-probe-loss bad-when 3 consecutive-probe-loss good-when 2 consecutive-probe-loss unreachable-when 10 ! policy-based-routing ip policy-route 10 from private.lan to private.peer linkmon-group tunnelgroup linkmon-profile tunnelquality policy-based-routing enable ! interface tunnel0 mtu 1500 tunnel source eth1 tunnel destination 172.16.0.1 tunnel local id 2 tunnel remote id 1 tunnel mode l2tp v3 ip address 192.168.100.2/30 ! interface tunnel1 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local id 4 tunnel remote id 3 tunnel protection ipsec tunnel mode l2tp v3 ip address 192.168.200.2/30 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.1.0/24 192.168.100.1 ip route 192.168.1.0/24 192.168.200.1 ! end
(C) 2022 - 2024 アライドテレシスホールディングス株式会社
PN: 613-003066 Rev.J