[index] AT-TQ7403-R コマンドリファレンス 5.5.5

| vap1.0 | 無線1 (2.4GHz) VAP0 | Network2 | WPAパーソナル | passphrase1 | WPA2 WPA3 |
| vap1.1 | 無線1 (2.4GHz) VAP1 | Sales2 | WPAエンタープライズ | - | WPA3 |
| vap1.2 | 無線1 (2.4GHz) VAP2 | Management2 | WPAエンタープライズ | - | WPA3 |
| vap2.0 | 無線2 (5GHz) VAP0 | Network5 | WPAパーソナル | passphrase17 | WPA2 WPA3 |
| vap2.1 | 無線2 (5GHz) VAP1 | Sales5 | WPAエンタープライズ | - | WPA3 |
| vap2.2 | 無線2 (5GHz) VAP2 | Management5 | WPAエンタープライズ | - | WPA3 |
| vap3.0 | 無線3 (6GHz) VAP0 | Network6 | WPAパーソナル | passphrase34 | WPA3 |
| vap3.1 | 無線3 (6GHz) VAP1 | Sales6 | WPAエンタープライズ | - | WPA3 |
| vap3.2 | 無線3 (6GHz) VAP2 | Management6 | WPAエンタープライズ | - | WPA3 |
NoteVAPインターフェースの命名規則については「インターフェース」/「一般設定」をご参照ください。
(AR4050S) |
|||
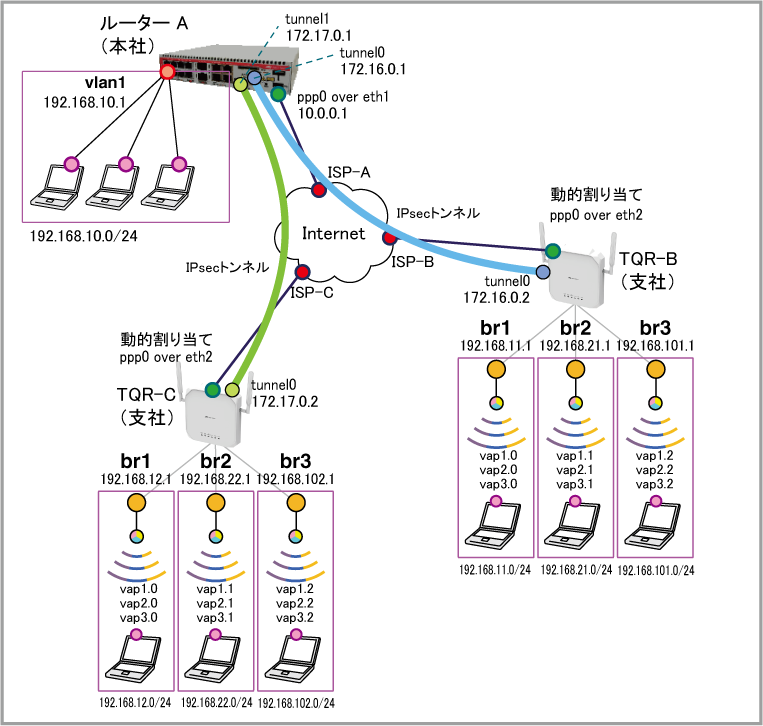
| ISP接続用ユーザー名 | user@ispA | user@ispB | user@ispC |
| ISP接続用パスワード | isppasswdA | isppasswdB | isppasswdC |
| PPPoEサービス名 | 指定なし | 指定なし | 指定なし |
| WAN側IPアドレス | 10.0.0.1/32 | 動的割り当て(IPCP) | 動的割り当て(IPCP) |
| br1 | - | vap1.0 vap2.0 vap3.0 | vap1.0 vap2.0 vap3.0 |
| br2 | - | vap1.1 vap2.1 vap3.1 | vap1.1 vap2.1 vap3.1 |
| br3 | - | vap1.2 vap2.2 vap3.2 | vap1.2 vap2.2 vap3.2 |
| WAN側物理インターフェース | eth1 | eth2 | eth2 |
| WAN側(ppp0)IPアドレス | 10.0.0.1/32 | 接続時にISPから取得 | 接続時にISPから取得 |
| LAN側(vlan1)IPアドレス | 192.168.10.1/24 | - | - |
| LAN側(br1)IPアドレス | - | 192.168.11.1/24 | 192.168.12.1/24 |
| LAN側(br2)IPアドレス | - | 192.168.21.1/24 | 192.168.22.1/24 |
| LAN側(br3)IPアドレス | - | 192.168.101.1/24 | 192.168.102.1/24 |
| アルゴリズム | |||
| ローカルID | 始点アドレス(デフォルト) | client_B | client_C |
| アルゴリズム | |||
| リース時間 | - | 2時間 | 2時間 |
| 対象サブネット | - | 192.168.11.0/24 | 192.168.12.0/24 |
| デフォルトゲートウェイ | - | 192.168.11.1 | 192.168.12.1 |
| DNSサーバー | - | 192.168.11.1 | 192.168.12.1 |
| 提供するIPアドレスの範囲 | - | 192.168.11.100~ 192.168.11.131(32個) |
192.168.12.100~ 192.168.12.131(32個) |
| リース時間 | - | 2時間 | 2時間 |
| 対象サブネット | - | 192.168.21.0/24 | 192.168.22.0/24 |
| デフォルトゲートウェイ | - | 192.168.21.1 | 192.168.22.1 |
| DNSサーバー | - | 192.168.21.1 | 192.168.22.1 |
| 提供するIPアドレスの範囲 | - | 192.168.21.100~ 192.168.21.131(32個) |
192.168.22.100~ 192.168.22.131(32個) |
| リース時間 | - | 2時間 | 2時間 |
| 対象サブネット | - | 192.168.101.0/24 | 192.168.102.0/24 |
| デフォルトゲートウェイ | - | 192.168.101.1 | 192.168.102.1 |
| DNSサーバー | - | 192.168.101.1 | 192.168.102.1 |
| 提供するIPアドレスの範囲 | - | 192.168.101.100~ 192.168.101.131(32個) |
192.168.102.100~ 192.168.102.131(32個) |
no spanning-tree rstp enable
interface eth1 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu
interface vlan1 ip address 192.168.10.1/24
zone private network lan ip subnet 172.16.0.0/30 ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.11.0/24 ip subnet 192.168.21.0/24 ip subnet 192.168.101.0/24 ip subnet 192.168.12.0/24 ip subnet 192.168.22.0/24 ip subnet 192.168.102.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0
application esp protocol 50
application isakmp protocol udp sport 500 dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret-ab hostname Client_B crypto isakmp key secret-ac hostname Client_C
crypto isakmp peer dynamic profile isakmp1
interface tunnel0 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 mtu 1300
interface tunnel1 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.1/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.11.0/24 tunnel0 ip route 192.168.11.0/24 null 254 ip route 192.168.12.0/24 tunnel1 ip route 192.168.12.0/24 null 254 ip route 192.168.21.0/24 tunnel0 ip route 192.168.21.0/24 null 254 ip route 192.168.22.0/24 tunnel1 ip route 192.168.22.0/24 null 254 ip route 192.168.101.0/24 tunnel0 ip route 192.168.101.0/24 null 254 ip route 192.168.102.0/24 tunnel1 ip route 192.168.102.0/24 null 254
end
wireless
security 1 mode wpa-personal key passphrase1 versions wpa2 wpa3 security 2 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 3 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 17 mode wpa-personal key passphrase17 versions wpa2 wpa3 security 18 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 19 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 34 mode wpa-personal key passphrase34 versions wpa3 security 35 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 36 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required
Note本設定例では、2.4GHz、5GHz、6GHzのVAPに別々のSSIDを設定していますが、各帯域のVAPに同じSSIDを設定し、バンドステアリングを有効にすることで、複数の帯域をサポートしている無線端末に対し、混雑していない帯域への接続を促し、帯域を有効に使うことができます。
具体的な設定については設定例集#201aをご参照ください。
network 1 ssid Network2 hide-ssid security 1 network 2 ssid Sales2 hide-ssid security 2 network 3 ssid Management2 hide-ssid security 3 network 17 ssid Network5 hide-ssid security 17 network 18 ssid Sales5 hide-ssid security 18 network 19 ssid Management5 hide-ssid security 19 network 34 ssid Network6 hide-ssid security 34 network 35 ssid Sales6 hide-ssid security 35 network 36 ssid Management6 hide-ssid security 36
ap-profile local radio 1 enable vap 0 network 1 vap 1 network 2 vap 2 network 3 radio 2 enable vap 0 network 17 vap 1 network 18 vap 2 network 19 radio 3 enable vap 0 network 34 vap 1 network 35 vap 2 network 36
radius-server local server enable nas 127.0.0.1 key awplus-local-radius-server user userA password passwdA user userB password passwdB user userC password passwdC
radius-server host 127.0.0.1 key awplus-local-radius-server
end wireless ap-configuration apply ap local configure terminal
bridge 1 bridge 2 bridge 3
Note本設定例では、2.4GHz、5GHz、6GHzの同一番号のVAPをブリッジに所属させ同じセグメントで運用しています。
各帯域のVAPを異なるセグメントで運用する場合は、VAPごとにブリッジを用意して(本例ではブリッジを6つ作成して)、各ブリッジにIPアドレスを設定し、エンティティーとファイアウォールの設定を変更してください。
interface vap1.0 bridge-group 1 interface vap1.1 bridge-group 2 interface vap1.2 bridge-group 3 interface vap2.0 bridge-group 1 interface vap2.1 bridge-group 2 interface vap2.2 bridge-group 3 interface vap3.0 bridge-group 1 interface vap3.1 bridge-group 2 interface vap3.2 bridge-group 3
end wireless ap-configuration apply ap local configure terminal
interface eth2 encapsulation ppp 0
interface ppp0 ppp ipcp dns request keepalive ppp username user@ispB ppp password isppasswdB ip address negotiated ip tcp adjust-mss pmtu
interface br1 ip address 192.168.11.1/24 interface br2 ip address 192.168.21.1/24 interface br3 ip address 192.168.101.1/24
zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 network lan1br1 ip subnet 192.168.11.0/24 network lan1br2 ip subnet 192.168.21.0/24 network lan1br3 ip subnet 192.168.101.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0
application esp protocol 50
application isakmp protocol udp sport 500 dport 500
firewall rule 10 deny any from private.lan1br1 to private.lan1br3 rule 20 deny any from private.lan1br2 to private.lan1br3 rule 30 permit any from private to private rule 40 permit any from private to public rule 50 permit isakmp from public.wan.ppp0 to public.wan rule 60 permit isakmp from public.wan to public.wan.ppp0 rule 70 permit esp from public.wan.ppp0 to public.wan rule 80 permit esp from public.wan to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
ip dhcp pool pool11 network 192.168.11.0 255.255.255.0 range 192.168.11.100 192.168.11.131 dns-server 192.168.11.1 default-router 192.168.11.1 lease 0 2 0 ip dhcp pool pool21 network 192.168.21.0 255.255.255.0 range 192.168.21.100 192.168.21.131 dns-server 192.168.21.1 default-router 192.168.21.1 lease 0 2 0 ip dhcp pool pool101 network 192.168.101.0 255.255.255.0 range 192.168.101.100 192.168.101.131 dns-server 192.168.101.1 default-router 192.168.101.1 lease 0 2 0
service dhcp-server
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret-ab address 10.0.0.1
crypto isakmp peer address 10.0.0.1 profile isakmp1
interface tunnel0 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 null 254
ip dns forwarding
end
wireless
security 1 mode wpa-personal key passphrase1 versions wpa2 wpa3 security 2 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 3 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 17 mode wpa-personal key passphrase17 versions wpa2 wpa3 security 18 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 19 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 34 mode wpa-personal key passphrase34 versions wpa3 security 35 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 36 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required
Note本設定例では、2.4GHz、5GHz、6GHzのVAPに別々のSSIDを設定していますが、各帯域のVAPに同じSSIDを設定し、バンドステアリングを有効にすることで、複数の帯域をサポートしている無線端末に対し、混雑していない帯域への接続を促し、帯域を有効に使うことができます。
具体的な設定については設定例集#201aをご参照ください。
network 1 ssid Network2 hide-ssid security 1 network 2 ssid Sales2 hide-ssid security 2 network 3 ssid Management2 hide-ssid security 3 network 17 ssid Network5 hide-ssid security 17 network 18 ssid Sales5 hide-ssid security 18 network 19 ssid Management5 hide-ssid security 19 network 34 ssid Network6 hide-ssid security 34 network 35 ssid Sales6 hide-ssid security 35 network 36 ssid Management6 hide-ssid security 36
ap-profile local radio 1 enable vap 0 network 1 vap 1 network 2 vap 2 network 3 radio 2 enable vap 0 network 17 vap 1 network 18 vap 2 network 19 radio 3 enable vap 0 network 34 vap 1 network 35 vap 2 network 36
radius-server local server enable nas 127.0.0.1 key awplus-local-radius-server user userA password passwdA user userB password passwdB user userC password passwdC
radius-server host 127.0.0.1 key awplus-local-radius-server
end wireless ap-configuration apply ap local configure terminal
bridge 1 bridge 2 bridge 3
Note本設定例では、2.4GHz、5GHz、6GHzの同一番号のVAPをブリッジに所属させ同じセグメントで運用しています。
各帯域のVAPを異なるセグメントで運用する場合は、VAPごとにブリッジを用意して(本例ではブリッジを6つ作成して)、各ブリッジにIPアドレスを設定し、エンティティーとファイアウォールの設定を変更してください。
interface vap1.0 bridge-group 1 interface vap1.1 bridge-group 2 interface vap1.2 bridge-group 3 interface vap2.0 bridge-group 1 interface vap2.1 bridge-group 2 interface vap2.2 bridge-group 3 interface vap3.0 bridge-group 1 interface vap3.1 bridge-group 2 interface vap3.2 bridge-group 3
end wireless ap-configuration apply ap local configure terminal
interface eth2 encapsulation ppp 0
interface ppp0 ppp ipcp dns request keepalive ppp username user@ispC ppp password isppasswdC ip address negotiated ip tcp adjust-mss pmtu
interface br1 ip address 192.168.12.1/24 interface br2 ip address 192.168.22.1/24 interface br3 ip address 192.168.102.1/24
zone private network lan ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 network lan2br1 ip subnet 192.168.12.0/24 network lan2br2 ip subnet 192.168.22.0/24 network lan2br3 ip subnet 192.168.102.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0
application esp protocol 50
application isakmp protocol udp sport 500 dport 500
firewall rule 10 deny any from private.lan2br1 to private.lan2br3 rule 20 deny any from private.lan2br2 to private.lan2br3 rule 30 permit any from private to private rule 40 permit any from private to public rule 50 permit isakmp from public.wan.ppp0 to public.wan rule 60 permit isakmp from public.wan to public.wan.ppp0 rule 70 permit esp from public.wan.ppp0 to public.wan rule 80 permit esp from public.wan to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
ip dhcp pool pool12 network 192.168.12.0 255.255.255.0 range 192.168.12.100 192.168.12.131 dns-server 192.168.12.1 default-router 192.168.12.1 lease 0 2 0 ip dhcp pool pool22 network 192.168.22.0 255.255.255.0 range 192.168.22.100 192.168.22.131 dns-server 192.168.22.1 default-router 192.168.22.1 lease 0 2 0 ip dhcp pool pool102 network 192.168.102.0 255.255.255.0 range 192.168.102.100 192.168.102.131 dns-server 192.168.102.1 default-router 192.168.102.1 lease 0 2 0
service dhcp-server
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 transform 2 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret-ac address 10.0.0.1
crypto isakmp peer address 10.0.0.1 profile isakmp1
interface tunnel0 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.2/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 null 254
ip dns forwarding
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility local5 ↓
awplus# show log | include Firewall ↓
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.10.1/24 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.11.0/24 ip subnet 192.168.21.0/24 ip subnet 192.168.101.0/24 ip subnet 192.168.12.0/24 ip subnet 192.168.22.0/24 ip subnet 192.168.102.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret-ab hostname Client_B crypto isakmp key secret-ac hostname Client_C ! crypto isakmp peer dynamic profile isakmp1 ! interface tunnel0 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 mtu 1300 ! interface tunnel1 tunnel source ppp0 tunnel destination dynamic tunnel remote name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.1/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.11.0/24 tunnel0 ip route 192.168.11.0/24 null 254 ip route 192.168.12.0/24 tunnel1 ip route 192.168.12.0/24 null 254 ip route 192.168.21.0/24 tunnel0 ip route 192.168.21.0/24 null 254 ip route 192.168.22.0/24 tunnel1 ip route 192.168.22.0/24 null 254 ip route 192.168.101.0/24 tunnel0 ip route 192.168.101.0/24 null 254 ip route 192.168.102.0/24 tunnel1 ip route 192.168.102.0/24 null 254 ! end
! wireless ! security 1 mode wpa-personal key passphrase1 versions wpa2 wpa3 security 2 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 3 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 17 mode wpa-personal key passphrase17 versions wpa2 wpa3 security 18 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 19 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 34 mode wpa-personal key passphrase34 versions wpa3 security 35 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 36 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required ! network 1 ssid Network2 hide-ssid security 1 network 2 ssid Sales2 hide-ssid security 2 network 3 ssid Management2 hide-ssid security 3 network 17 ssid Network5 hide-ssid security 17 network 18 ssid Sales5 hide-ssid security 18 network 19 ssid Management5 hide-ssid security 19 network 34 ssid Network6 hide-ssid security 34 network 35 ssid Sales6 hide-ssid security 35 network 36 ssid Management6 hide-ssid security 36 ! ap-profile local radio 1 enable vap 0 network 1 vap 1 network 2 vap 2 network 3 radio 2 enable vap 0 network 17 vap 1 network 18 vap 2 network 19 radio 3 enable vap 0 network 34 vap 1 network 35 vap 2 network 36 ! radius-server local server enable nas 127.0.0.1 key awplus-local-radius-server user userA password passwdA user userB password passwdB user userC password passwdC ! radius-server host 127.0.0.1 key awplus-local-radius-server ! bridge 1 bridge 2 bridge 3 ! interface vap1.0 bridge-group 1 interface vap1.1 bridge-group 2 interface vap1.2 bridge-group 3 interface vap2.0 bridge-group 1 interface vap2.1 bridge-group 2 interface vap2.2 bridge-group 3 interface vap3.0 bridge-group 1 interface vap3.1 bridge-group 2 interface vap3.2 bridge-group 3 ! interface eth2 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ppp username user@ispB ppp password isppasswdB ip address negotiated ip tcp adjust-mss pmtu ! interface br1 ip address 192.168.11.1/24 interface br2 ip address 192.168.21.1/24 interface br3 ip address 192.168.101.1/24 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 network lan1br1 ip subnet 192.168.11.0/24 network lan1br2 ip subnet 192.168.21.0/24 network lan1br3 ip subnet 192.168.101.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 deny any from private.lan1br1 to private.lan1br3 rule 20 deny any from private.lan1br2 to private.lan1br3 rule 30 permit any from private to private rule 40 permit any from private to public rule 50 permit isakmp from public.wan.ppp0 to public.wan rule 60 permit isakmp from public.wan to public.wan.ppp0 rule 70 permit esp from public.wan.ppp0 to public.wan rule 80 permit esp from public.wan to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! ip dhcp pool pool11 network 192.168.11.0 255.255.255.0 range 192.168.11.100 192.168.11.131 dns-server 192.168.11.1 default-router 192.168.11.1 lease 0 2 0 ip dhcp pool pool21 network 192.168.21.0 255.255.255.0 range 192.168.21.100 192.168.21.131 dns-server 192.168.21.1 default-router 192.168.21.1 lease 0 2 0 ip dhcp pool pool101 network 192.168.101.0 255.255.255.0 range 192.168.101.100 192.168.101.131 dns-server 192.168.101.1 default-router 192.168.101.1 lease 0 2 0 ! service dhcp-server ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 transform 1 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret-ab address 10.0.0.1 ! crypto isakmp peer address 10.0.0.1 profile isakmp1 ! interface tunnel0 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_B tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 null 254 ! ip dns forwarding ! end
! wireless ! security 1 mode wpa-personal key passphrase1 versions wpa2 wpa3 security 2 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 3 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 17 mode wpa-personal key passphrase17 versions wpa2 wpa3 security 18 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 19 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 34 mode wpa-personal key passphrase34 versions wpa3 security 35 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required security 36 mode wpa-enterprise versions wpa3 radius authentication group radius management-frame-protection enable type required ! network 1 ssid Network2 hide-ssid security 1 network 2 ssid Sales2 hide-ssid security 2 network 3 ssid Management2 hide-ssid security 3 network 17 ssid Network5 hide-ssid security 17 network 18 ssid Sales5 hide-ssid security 18 network 19 ssid Management5 hide-ssid security 19 network 34 ssid Network6 hide-ssid security 34 network 35 ssid Sales6 hide-ssid security 35 network 36 ssid Management6 hide-ssid security 36 ! ap-profile local radio 1 enable vap 0 network 1 vap 1 network 2 vap 2 network 3 radio 2 enable vap 0 network 17 vap 1 network 18 vap 2 network 19 radio 3 enable vap 0 network 34 vap 1 network 35 vap 2 network 36 ! radius-server local server enable nas 127.0.0.1 key awplus-local-radius-server user userA password passwdA user userB password passwdB user userC password passwdC ! radius-server host 127.0.0.1 key awplus-local-radius-server ! bridge 1 bridge 2 bridge 3 ! interface vap1.0 bridge-group 1 interface vap1.1 bridge-group 2 interface vap1.2 bridge-group 3 interface vap2.0 bridge-group 1 interface vap2.1 bridge-group 2 interface vap2.2 bridge-group 3 interface vap3.0 bridge-group 1 interface vap3.1 bridge-group 2 interface vap3.2 bridge-group 3 ! interface eth2 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ppp username user@ispC ppp password isppasswdC ip address negotiated ip tcp adjust-mss pmtu ! interface br1 ip address 192.168.12.1/24 interface br2 ip address 192.168.22.1/24 interface br3 ip address 192.168.102.1/24 ! zone private network lan ip subnet 172.17.0.0/30 ip subnet 192.168.10.0/24 network lan2br1 ip subnet 192.168.12.0/24 network lan2br2 ip subnet 192.168.22.0/24 network lan2br3 ip subnet 192.168.102.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address dynamic interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 deny any from private.lan2br1 to private.lan2br3 rule 20 deny any from private.lan2br2 to private.lan2br3 rule 30 permit any from private to private rule 40 permit any from private to public rule 50 permit isakmp from public.wan.ppp0 to public.wan rule 60 permit isakmp from public.wan to public.wan.ppp0 rule 70 permit esp from public.wan.ppp0 to public.wan rule 80 permit esp from public.wan to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! ip dhcp pool pool12 network 192.168.12.0 255.255.255.0 range 192.168.12.100 192.168.12.131 dns-server 192.168.12.1 default-router 192.168.12.1 lease 0 2 0 ip dhcp pool pool22 network 192.168.22.0 255.255.255.0 range 192.168.22.100 192.168.22.131 dns-server 192.168.22.1 default-router 192.168.22.1 lease 0 2 0 ip dhcp pool pool102 network 192.168.102.0 255.255.255.0 range 192.168.102.100 192.168.102.131 dns-server 192.168.102.1 default-router 192.168.102.1 lease 0 2 0 ! service dhcp-server ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 transform 2 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret-ac address 10.0.0.1 ! crypto isakmp peer address 10.0.0.1 profile isakmp1 ! interface tunnel0 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local name Client_C tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.17.0.2/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 null 254 ! ip dns forwarding ! end
(C) 2024-2025 アライドテレシスホールディングス株式会社
PN: 613-003360 Rev.C