<前頁 次頁> << >> ↓ 目次 (番号順 (詳細)・ 回線別 (詳細)・ 機能別 (詳細))
CentreCOM ARX640S 設定例集 5.1.5 #25
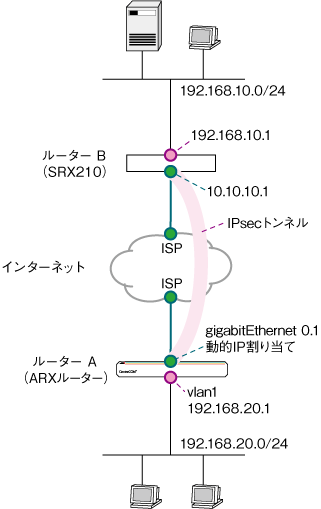
PPPoEでインターネットに接続している拠点間をIPsecで結ぶVPN構築例です。インターネットサービスプロバイダー(以下 ISP)から動的にIPアドレスが割り当てられるルーター(ルーターA:ARXルーター)と固定IPアドレスが割り当てられているルーター(ルーターB:SRX210)をIPsec(ESP)トンネルで接続します。

| PPPユーザー名 | user2@example | user1@example |
| PPPパスワード | password | |
| PPPoEサービス名 | 指定なし | |
| 使用できるIPアドレス | グローバルアドレス1個(動的割り当て) | 10.10.10.1/32 |
| 接続形態 | 端末型(アドレス1個不定) | 端末型(アドレス1個固定) |
| DNSサーバー | 接続時に通知される | |
| WAN側物理インターフェース | gigabitEthernet 0 | ge-0/0/0 |
| WAN側IPアドレス | 動的割り当て | 10.10.10.1/32 |
| LAN側IPアドレス | 192.168.20.1/24 | 192.168.10.1/24 |
| VPN接続設定 | ||
| ローカルセキュアグループ | 192.168.20.0/24 | 192.168.10.0/24 |
| リモートセキュアグループ | 192.168.10.0/24 | 192.168.20.0/24 |
| トンネル終端アドレス | 10.10.10.1 | ANY |
| IKE設定 | ||
| 交換モード | Aggressiveモード | |
| 認証方式 | 事前共有鍵(pre-shared key) | |
| 事前共有鍵 | secret(文字列) | |
| ローカルID/リモートID | client/なし | なし/client |
| 暗号化認証アルゴリズム | 3DES & SHA1-DH2 | |
| 有効期限 | 3600秒(1時間) | 3600秒(1時間)(デフォルト) |
| DPDによる死活監視 | 行う | |
| 起動時のISAKMPネゴシエーション | 行う | |
| IPsec設定 | ||
| SAモード | トンネルモード | |
| セキュリティープロトコル | ESP | |
| 暗号化認証アルゴリズム | 3DES & SHA1 | |
| PFSグループ | なし | |
| 有効期限 | 3600秒(1時間)(デフォルト) | |
| ルーターAの設定 |
ppp profile pppoe0 ↓
my-username user2@example password password ↓
interface gigabitEthernet 0 ↓
no shutdown ↓
interface gigabitEthernet 0.1 ↓
ip address ipcp ↓
ip tcp mss auto ↓
no shutdown ↓
pppoe enable ↓
ppp bind-profile pppoe0 ↓
ip napt inside any ↓
ip ids in protect ↓
interface vlan 1 ↓
ip address 192.168.20.1/24 ↓
ip address-up-always ↓
ip route default gigabitEthernet 0.1 ↓
access-list ip extended pppoe0-in ↓
access-list ip extended pppoe0-out ↓
dynamic permit ip any any ↓
interface gigabitEthernet 0.1 ↓
ip traffic-filter pppoe0-in in ↓
ip traffic-filter pppoe0-out out ↓
isakmp proposal isakmp encryption 3des hash sha1 group 2 ↓
isakmp proposal isakmp lifetime 3600 ↓
isakmp policy i ↓
peer 10.10.10.1 ↓
mode aggressive ↓
auth preshared key secret ↓
local-id client ↓
proposal isakmp ↓
keepalive enable ↓
access-list ip extended ipsec ↓
permit ip any any ↓
ipsec proposal ipsec esp encryption 3des hash sha1 ↓
ipsec policy vpn ↓
peer 10.10.10.1 ↓
access-list ipsec ↓
local-id 192.168.20.0/24 ↓
remote-id 192.168.10.0/24 ↓
proposal ipsec ↓
always-up-sa ↓
interface tunnel 0 ↓
tunnel mode ipsec ↓
ip unnumbered vlan 1 ↓
ip tcp mss auto ↓
no shutdown ↓
tunnel policy vpn ↓
ip route 192.168.10.0/24 tunnel 0 ↓
ip route 192.168.10.0/24 Null 254 ↓
proxydns ip enable ↓
copy running-config startup-config ↓
| ルーターBの設定 |
rout@% cli ↓
root> configure ↓
Note - コンフィグレーションモードで設定したコンフィグは「Candidate Config(候補設定)」に保存されるだけであり、運用中の設定「Active Config」に保存されるわけではありません。「Candidate Config」の設定を「Active Config」に反映するには、最後に「commit」コマンドを使用します。
root# delete ↓
This will delete the entire configuration ↓
Delete everything under this level? [yes,no] (no) yes ↓
root# set system root-authentication plain-text-password ↓
New password: PasswordS ↓
Retype new password: PasswordS ↓
Note - 本設定を行わないと「Candidate Config」を「Active Config」に反映する「commit」コマンドが使用できません。
root# set interfaces ge-0/0/1 unit 0 family inet address 192.168.10.1/24 ↓
root# set interfaces ge-0/0/0 unit 0 encapsulation ppp-over-ether ↓
root# set interfaces pp0 unit 0 ppp-options chap local-name user1@example default-chap-secret password passive ↓
root# set interfaces pp0 unit 0 pppoe-options underlying-interface ge-0/0/0.0 auto-reconnect 10 client ↓
root# set interfaces pp0 unit 0 family inet negotiate-address ↓
root# set routing-options static route 0.0.0.0/0 next-hop pp0.0 ↓
root# set security zones security-zone trust interfaces ge-0/0/1.0 ↓
root# set security zones security-zone untrust interfaces pp0.0 ↓
root# set security zones security-zone trust host-inbound-traffic system-services all ↓
root# set security zones security-zone untrust host-inbound-traffic system-services ping ↓
root# set security zones security-zone untrust host-inbound-traffic system-services ike ↓
root# edit security nat source rule-set TrustToUntrust ↓
root# set from zone trust ↓
root# set to zone untrust ↓
root# set rule match1 match source-address 0.0.0.0/0 ↓
root# set rule match1 then source-nat interface ↓
root# top ↓
root# set security zones security-zone trust address-book address net10 192.168.10.0/24 ↓
root# set security zones security-zone trust address-book address net20 192.168.20.0/24 ↓
root# set interfaces st0 unit 0 family inet ↓
root# set security zones security-zone trust interfaces st0.0 ↓
root# set security ike respond-bad-spi 5 ↓
root# set security ike proposal ar-p1 authentication-method pre-shared-keys ↓
root# set security ike proposal ar-p1 dh-group group2 ↓
root# set security ike proposal ar-p1 encryption-algorithm 3des-cbc ↓
root# set security ike proposal ar-p1 authentication-algorithm sha1 ↓
root# set security ike proposal ar-p1 lifetime-seconds 3600 ↓
root# set security ipsec proposal ar-p2 protocol esp ↓
root# set security ipsec proposal ar-p2 encryption-algorithm 3des-cbc ↓
root# set security ipsec proposal ar-p2 authentication-algorithm hmac-sha1-96 ↓
root# set security ipsec proposal ar-p2 lifetime-seconds 3600 ↓
root# set security ike policy p1-policy mode aggressive ↓
root# set security ike policy p1-policy proposals ar-p1 ↓
root# set security ike policy p1-policy pre-shared-key ascii-text secret ↓
set security ipsec policy p2-policy proposals ar-p2 ↓
root# set security ike gateway ar-gw ike-policy p1-policy ↓
root# set security ike gateway ar-gw dynamic hostname client ↓
root# set security ike gateway ar-gw external-interface pp0.0 ↓
root# set security ike gateway ar-gw dead-peer-detection always-send interval 20 threshold 5 ↓
root# set security ipsec vpn ar-vpn ike gateway ar-gw ↓
root# set security ipsec vpn ar-vpn ike ipsec-policy p2-policy ↓
root# set security ipsec vpn ar-vpn establish-tunnels immediately ↓
root# set security ipsec vpn ar-vpn bind-interface st0.0 ↓
root# set security ipsec vpn ar-vpn ike proxy-identity local 192.168.10.0/24 ↓
root# set security ipsec vpn ar-vpn ike proxy-identity remote 192.168.20.0/24 ↓
root# set security ipsec vpn ar-vpn ike proxy-identity service any ↓
root# edit security policies from-zone trust to-zone trust policy vpn-policy ↓
root# set match source-address net10 ↓
root# set match destination-address net20 ↓
root# set match application any ↓
root# set then permit ↓
root# top ↓
root# edit security policies from-zone trust to-zone trust policy vpn-policy-re ↓
root# set match source-address net20 ↓
root# set match destination-address net10 ↓
root# set match application any ↓
root# set then permit ↓
root# top ↓
root# set routing-options static route 192.168.20.0/24 next-hop st0.0 ↓
root# commit ↓
| まとめ |
ルーターAのコンフィグ
! service password-encryption ! clock timezone JST 9 ! ! ip address-up-always ppp profile pppoe0 my-username user2@example password 8 e$QOccTYhEXbMdnN4uqTQgYCAAA ! interface gigabitEthernet 0 no shutdown ! interface gigabitEthernet 0.1 ip address ipcp ip tcp mss auto no shutdown pppoe enable ppp bind-profile pppoe0 ip napt inside any ip traffic-filter pppoe0-in in ip traffic-filter pppoe0-out out ip ids in protect ! interface gigabitEthernet 1 shutdown ! interface gigabitEthernet 2 no shutdown ! interface gigabitEthernet 3 no shutdown ! interface gigabitEthernet 4 no shutdown ! interface gigabitEthernet 5 no shutdown ! interface loop 0 shutdown ! interface loop 1 shutdown ! interface tunnel 0 tunnel mode ipsec ip unnumbered vlan 1 ip tcp mss auto no shutdown tunnel policy vpn ! interface vlan 1 ip address 192.168.20.1/24 no shutdown ! ip route default gigabitEthernet 0.1 ip route 192.168.10.0/24 tunnel 0 ip route 192.168.10.0/24 Null 254 ! access-list ip extended ipsec permit ip any any access-list ip extended pppoe0-in access-list ip extended pppoe0-out dynamic permit ip any any ! isakmp proposal isakmp encryption 3des hash sha1 group 2 isakmp proposal isakmp lifetime 3600 ! isakmp policy i peer 10.10.10.1 mode aggressive auth preshared key 8 e$I3eQu7yNuLxQA local-id client proposal isakmp keepalive enable ! ipsec proposal ipsec esp encryption 3des hash sha1 ! ipsec policy vpn peer 10.10.10.1 access-list ipsec local-id 192.168.20.0/24 remote-id 192.168.10.0/24 proposal ipsec always-up-sa ! proxydns ip enable ! ! ! end |
ルーターBのコンフィグ
version 10.4R3.4;
system {
root-authentication {
encrypted-password "$1$2iO176Qb$3HdbjwWOKzsW5.m.rRgC4."; ## SECRET-DATA
}
}
interfaces {
ge-0/0/0 {
unit 0 {
encapsulation ppp-over-ether;
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.10.1/24;
}
}
}
pp0 {
unit 0 {
ppp-options {
chap {
default-chap-secret "$9$ECDhlM8LNbYoxNmT39OBxNdVwg"; ## SECRET-DATA
local-name "user1@example";
passive;
}
}
pppoe-options {
underlying-interface ge-0/0/0.0;
auto-reconnect 10;
client;
}
family inet {
negotiate-address;
}
}
}
st0 {
unit 0 {
family inet;
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop pp0.0;
route 192.168.20.0/24 next-hop st0.0;
}
}
security {
ike {
respond-bad-spi 5;
proposal ar-p1 {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
lifetime-seconds 3600;
}
policy p1-policy {
mode aggressive;
proposals ar-p1;
pre-shared-key ascii-text "$9$wqgZjmPQn6Amf39CtRE"; ## SECRET-DATA
}
gateway ar-gw {
ike-policy p1-policy;
dynamic hostname client;
dead-peer-detection {
always-send;
interval 20;
threshold 5;
}
external-interface pp0.0;
}
}
ipsec {
proposal ar-p2 {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 3600;
}
policy p2-policy {
proposals ar-p2;
}
vpn ar-vpn {
bind-interface st0.0;
ike {
gateway ar-gw;
proxy-identity {
local 192.168.10.0/24;
remote 192.168.20.0/24;
service any;
}
ipsec-policy p2-policy;
}
establish-tunnels immediately;
}
}
nat {
source {
rule-set TrustToUntrust {
from zone trust;
to zone untrust;
rule match1 {
match {
source-address 0.0.0.0/0;
}
then {
source-nat {
interface;
}
}
}
}
}
}
zones {
security-zone trust {
address-book {
address net10 192.168.10.0/24;
address net20 192.168.20.0/24;
}
host-inbound-traffic {
system-services {
all;
}
}
interfaces {
ge-0/0/1.0;
st0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ping;
ike;
}
}
interfaces {
pp0.0;
}
}
}
policies {
from-zone trust to-zone trust {
policy vpn-policy {
match {
source-address net10;
destination-address net20;
application any;
}
then {
permit;
}
}
policy vpn-policy-re {
match {
source-address net20;
destination-address net10;
application any;
}
then {
permit;
}
}
}
}
}
|
(C) 2011-2014 アライドテレシスホールディングス株式会社
PN: 613-001568 Rev.E