[index] AT-AR3050S/AT-AR4050S コマンドリファレンス 5.4.5
Note - IPレピュテーション(IPアドレスブラックリスト)機能を使用するにはサブスクリプションライセンスが必要です。

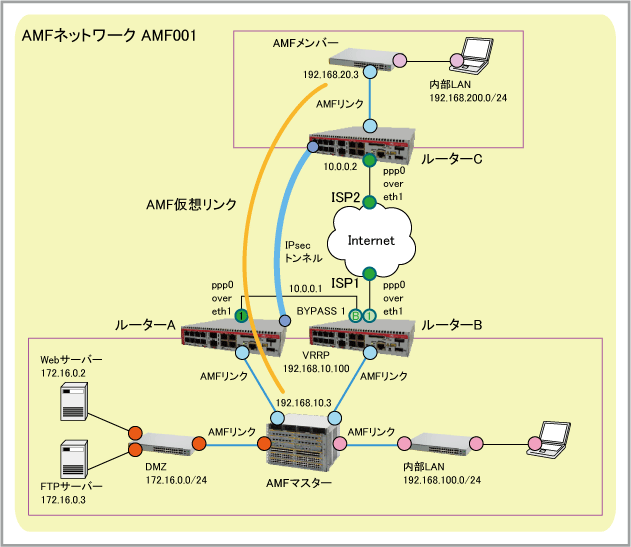
| AMFネットワーク名 | AMF001 | ||
| AMF仮想リンク | 192.168.10.3(AMFマスター) - 192.168.20.3(AMFメンバー) | ||
(実際に接続するのはVRRPマスターのみ) |
|||
| ISP接続用ユーザー名 | user@isp1(共通) | user@isp2 | |
| ISP接続用パスワード | isppasswd1(共通) | isppasswd2 | |
| PPPoEサービス名 | 指定なし(共通) | 指定なし | |
| WAN側IPアドレス | 10.0.0.1/32(共通) | 10.0.0.2/32 | |
| DNSサーバーIPアドレス | 自動取得(IPCP)(共通) | 自動取得(IPCP) | |
| WAN側物理インターフェース | eth1 | eth1 | eth1 |
| WAN側(ppp0)IPアドレス | 10.0.0.1/32(VRRPマスター側でのみ有効) | 10.0.0.2/32 | |
| LAN側(vlan1)IPアドレス | 192.168.10.1/24 | 192.168.10.2/24 | 192.168.20.1/24 |
Note - ルーターA/Bのうち、VRRPマスタールーターとして動作しているほうが実際にIPsec接続を行います。
no spanning-tree rstp enable |
interface eth1 encapsulation ppp 0 |
interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp1 ppp password isppasswd1 ip tcp adjust-mss 1414 |
vlan database vlan 10 state enable |
hostname RouterA |
atmf network-name AMF001 |
interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 10 |
interface vlan10 ip address 192.168.10.1/24 |
router vrrp 10 vlan10 virtual-ip 192.168.10.100 backup priority 101 ha associate enable |
ips category checksum action deny protect |
ip-reputation provider emerging-threats protect |
zone dmz network servers ip subnet 172.16.0.0/16 host web ip address 172.16.0.2 host ftp ip address 172.16.0.3 |
zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 |
zone private network lan ip subnet 192.168.10.0/24 ip subnet 192.168.100.0/24 network peer ip subnet 192.168.20.0/24 ip subnet 192.168.200.0/24 network tunnel ip subnet 192.168.30.0/30 |
zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 |
application esp protocol 50 |
application isakmp protocol udp sport 500 dport 500 |
firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private rule 50 permit any from private to dmz rule 60 permit http from public to dmz.servers.web rule 70 permit ftp from public to dmz.servers.ftp rule 80 permit any from dmz to dmz rule 90 permit any from private to public rule 100 permit any from dmz to public rule 110 permit dns from public.ppp0 to public rule 120 permit https from public.ppp0 to public protect |
nat rule 10 masq any from private to public rule 20 masq any from dmz to public rule 30 portfw http from public with dst dmz.servers.web rule 40 portfw ftp from public with dst dmz.servers.ftp enable |
crypto isakmp key secret address 10.0.0.2 |
interface tunnel0 ip address 192.168.30.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel mode ipsec ipv4 tunnel protection ipsec |
ip route 0.0.0.0/0 ppp0 ip route 172.16.0.0/16 192.168.10.3 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 ip route 192.168.100.0/24 192.168.10.3 ip route 192.168.200.0/24 tunnel0 ip route 192.168.200.0/24 Null 254 |
ip dns forwarding |
end |
no spanning-tree rstp enable |
interface eth1 encapsulation ppp 0 |
interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp1 ppp password isppasswd1 ip tcp adjust-mss 1414 |
vlan database vlan 10 state enable |
hostname RouterB |
atmf network-name AMF001 |
interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 10 |
interface vlan10 ip address 192.168.10.2/24 |
router vrrp 10 vlan10 virtual-ip 192.168.10.100 backup ha associate wan-bypass 1 enable |
ips category checksum action deny protect |
ip-reputation provider emerging-threats protect |
zone dmz network servers ip subnet 172.16.0.0/16 host web ip address 172.16.0.2 host ftp ip address 172.16.0.3 |
zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 |
zone private network lan ip subnet 192.168.10.0/24 ip subnet 192.168.100.0/24 network peer ip subnet 192.168.20.0/24 ip subnet 192.168.200.0/24 network tunnel ip subnet 192.168.30.0/30 |
zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 |
application esp protocol 50 |
application isakmp protocol udp sport 500 dport 500 |
firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private rule 50 permit any from private to dmz rule 60 permit http from public to dmz.servers.web rule 70 permit ftp from public to dmz.servers.ftp rule 80 permit any from dmz to dmz rule 90 permit any from private to public rule 100 permit any from dmz to public rule 110 permit dns from public.ppp0 to public rule 120 permit https from public.ppp0 to public protect |
nat rule 10 masq any from private to public rule 20 masq any from dmz to public rule 30 portfw http from public with dst dmz.servers.web rule 40 portfw ftp from public with dst dmz.servers.ftp enable |
crypto isakmp key secret address 10.0.0.2 |
interface tunnel0 ip address 192.168.30.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel mode ipsec ipv4 tunnel protection ipsec |
ip route 0.0.0.0/0 ppp0 ip route 172.16.0.0/16 192.168.10.3 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 ip route 192.168.100.0/24 192.168.10.3 ip route 192.168.200.0/24 tunnel0 ip route 192.168.200.0/24 Null 254 |
ip dns forwarding |
end |
no spanning-tree rstp enable |
interface eth1 encapsulation ppp 0 |
interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp2 ppp password isppasswd2 ip tcp adjust-mss 1414 |
vlan database vlan 20 state enable |
hostname RouterC |
atmf network-name AMF001 |
interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 20 |
interface vlan20 ip address 192.168.20.1/24 |
ips category checksum action deny protect |
ip-reputation provider emerging-threats protect |
zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 |
zone private network lan ip subnet 192.168.20.0/24 ip subnet 192.168.200.0/24 network peer ip subnet 172.16.0.0/24 ip subnet 192.168.10.0/24 ip subnet 192.168.100.0/24 network tunnel ip subnet 192.168.30.0/30 |
zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 |
application esp protocol 50 |
application isakmp protocol udp sport 500 dport 500 |
firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private rule 50 permit any from private to public rule 60 permit dns from public.ppp0 to public rule 70 permit https from public.ppp0 to public protect |
nat rule 10 masq any from private to public enable |
crypto isakmp key secret address 10.0.0.1 |
interface tunnel0 ip address 192.168.30.2/30 tunnel source 10.0.0.2 tunnel destination 10.0.0.1 tunnel mode ipsec ipv4 tunnel protection ipsec |
ip route 0.0.0.0/0 ppp0 ip route 172.16.0.0/24 tunnel0 ip route 172.16.0.0/24 Null 254 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 Null 254 ip route 192.168.100.0/24 tunnel0 ip route 192.168.100.0/24 Null 254 ip route 192.168.200.0/24 192.168.20.3 |
ip dns forwarding |
end |
awplus# copy running-config startup-config ↓ Building configuration... [OK] |
awplus# write memory ↓ Building configuration... [OK] |
Note - 仮想リンクが設定されている構成図中「AMFメンバー」スイッチは、隣接するノード(ルーターC)の補助によりオートリカバリーが可能です。詳細は、AMF運用編の「仮想リンク経由で接続しているAMFノードのオートリカバリー」をご覧ください。なお、「AMFメンバー」スイッチをオートリカバリーするためには、ルーターCのインターネット接続とIPsecトンネル接続が確立されている必要があります。
Note - 一般的な手順については、AMF応用編の「拠点側ルーターの手動リカバリー」をご参照ください。
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp2 ppp password isppasswd2 ip tcp adjust-mss 1414 ! vlan database vlan 20 state enable ! atmf network-name AMF001 ! interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 20 ! interface vlan20 ip address 192.168.20.1/24 ! zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 ! zone private network lan ip subnet 192.168.20.0/24 network peer ip subnet 192.168.10.0/24 network tunnel ip subnet 192.168.30.0/30 ! zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret address 10.0.0.1 ! interface tunnel0 ip address 192.168.30.2/30 tunnel source 10.0.0.2 tunnel destination 10.0.0.1 tunnel mode ipsec ipv4 tunnel protection ipsec ! ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 Null 254 ! |
awplus# atmf recover RouterC ↓ |
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp1 ppp password isppasswd1 ip tcp adjust-mss 1414 ! vlan database vlan 10 state enable ! hostname RouterA ! atmf network-name AMF001 ! interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 10 ! interface vlan10 ip address 192.168.10.1/24 ! router vrrp 10 vlan10 virtual-ip 192.168.10.100 backup priority 101 ha associate enable ! ips category checksum action deny protect ! ip-reputation provider emerging-threats protect ! zone dmz network servers ip subnet 172.16.0.0/16 host web ip address 172.16.0.2 host ftp ip address 172.16.0.3 ! zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 ! zone private network lan ip subnet 192.168.10.0/24 ip subnet 192.168.100.0/24 network peer ip subnet 192.168.20.0/24 ip subnet 192.168.200.0/24 network tunnel ip subnet 192.168.30.0/30 ! zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private rule 50 permit any from private to dmz rule 60 permit http from public to dmz.servers.web rule 70 permit ftp from public to dmz.servers.ftp rule 80 permit any from dmz to dmz rule 90 permit any from private to public rule 100 permit any from dmz to public rule 110 permit dns from public.ppp0 to public rule 120 permit https from public.ppp0 to public protect ! nat rule 10 masq any from private to public rule 20 masq any from dmz to public rule 30 portfw http from public with dst dmz.servers.web rule 40 portfw ftp from public with dst dmz.servers.ftp enable ! crypto isakmp key secret address 10.0.0.2 ! interface tunnel0 ip address 192.168.30.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel mode ipsec ipv4 tunnel protection ipsec ! ip route 0.0.0.0/0 ppp0 ip route 172.16.0.0/16 192.168.10.3 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 ip route 192.168.100.0/24 192.168.10.3 ip route 192.168.200.0/24 tunnel0 ip route 192.168.200.0/24 Null 254 ! ip dns forwarding ! end |
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp1 ppp password isppasswd1 ip tcp adjust-mss 1414 ! vlan database vlan 10 state enable ! hostname RouterB ! atmf network-name AMF001 ! interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 10 ! interface vlan10 ip address 192.168.10.2/24 ! router vrrp 10 vlan10 virtual-ip 192.168.10.100 backup ha associate wan-bypass 1 enable ! ips category checksum action deny protect ! ip-reputation provider emerging-threats protect ! zone dmz network servers ip subnet 172.16.0.0/16 host web ip address 172.16.0.2 host ftp ip address 172.16.0.3 ! zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 ! zone private network lan ip subnet 192.168.10.0/24 ip subnet 192.168.100.0/24 network peer ip subnet 192.168.20.0/24 ip subnet 192.168.200.0/24 network tunnel ip subnet 192.168.30.0/30 ! zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private rule 50 permit any from private to dmz rule 60 permit http from public to dmz.servers.web rule 70 permit ftp from public to dmz.servers.ftp rule 80 permit any from dmz to dmz rule 90 permit any from private to public rule 100 permit any from dmz to public rule 110 permit dns from public.ppp0 to public rule 120 permit https from public.ppp0 to public protect ! nat rule 10 masq any from private to public rule 20 masq any from dmz to public rule 30 portfw http from public with dst dmz.servers.web rule 40 portfw ftp from public with dst dmz.servers.ftp enable ! crypto isakmp key secret address 10.0.0.2 ! interface tunnel0 ip address 192.168.30.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel mode ipsec ipv4 tunnel protection ipsec ! ip route 0.0.0.0/0 ppp0 ip route 172.16.0.0/16 192.168.10.3 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 ip route 192.168.100.0/24 192.168.10.3 ip route 192.168.200.0/24 tunnel0 ip route 192.168.200.0/24 Null 254 ! ip dns forwarding ! end |
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@isp2 ppp password isppasswd2 ip tcp adjust-mss 1414 ! vlan database vlan 20 state enable ! hostname RouterC ! atmf network-name AMF001 ! interface port1.0.1 switchport switchport atmf-link switchport mode trunk switchport trunk allowed vlan add 20 ! interface vlan20 ip address 192.168.20.1/24 ! ips category checksum action deny protect ! ip-reputation provider emerging-threats protect ! zone lan-atmf network atmf-link ip subnet 172.31.0.0/16 ! zone private network lan ip subnet 192.168.20.0/24 ip subnet 192.168.200.0/24 network peer ip subnet 172.16.0.0/24 ip subnet 192.168.10.0/24 ip subnet 192.168.100.0/24 network tunnel ip subnet 192.168.30.0/30 ! zone public network ppp0 ip subnet 0.0.0.0/0 interface ppp0 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit isakmp from public.ppp0 to public.ppp0 rule 20 permit esp from public.ppp0 to public.ppp0 rule 30 permit any from lan-atmf to lan-atmf rule 40 permit any from private to private rule 50 permit any from private to public rule 60 permit dns from public.ppp0 to public rule 70 permit https from public.ppp0 to public protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret address 10.0.0.1 ! interface tunnel0 ip address 192.168.30.2/30 tunnel source 10.0.0.2 tunnel destination 10.0.0.1 tunnel mode ipsec ipv4 tunnel protection ipsec ! ip route 0.0.0.0/0 ppp0 ip route 172.16.0.0/24 tunnel0 ip route 172.16.0.0/24 Null 254 ip route 192.168.10.0/24 tunnel0 ip route 192.168.10.0/24 Null 254 ip route 192.168.100.0/24 tunnel0 ip route 192.168.100.0/24 Null 254 ip route 192.168.200.0/24 192.168.20.3 ! ip dns forwarding ! end |
(C) 2015 アライドテレシスホールディングス株式会社
PN: 613-002107 Rev.E