<前頁 次頁> << >> ↓ 目次 (番号順 (詳細)・ 回線別 (詳細)・ 機能別 (詳細))
CentreCOM ARX640S 設定例集 5.1.5 #35
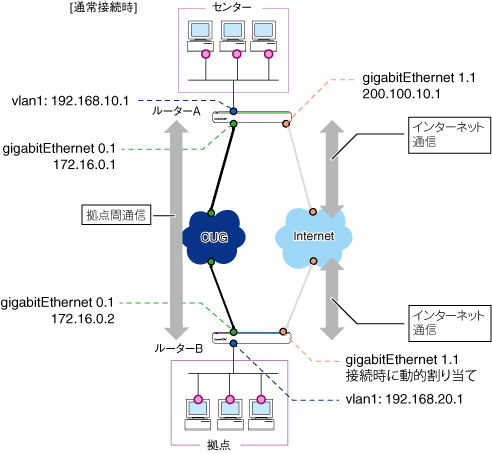
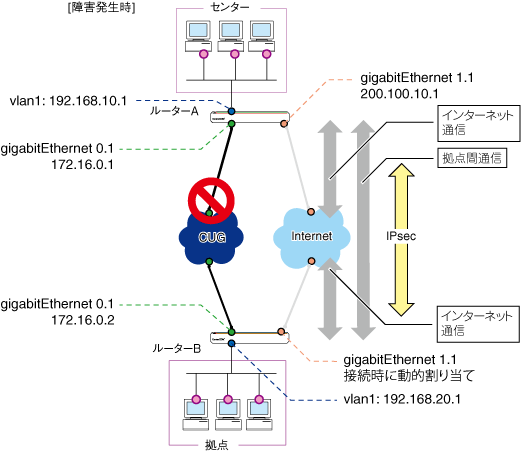
CUG(Closed Users Group)サービス(フレッツ・VPNワイド、フレッツ・グループアクセス(NTT東日本)、フレッツ・グループ(NTT西日本)など)とインターネット回線を利用し、CUGをメイン回線、インターネットをバックアップ回線として使用します。CUG側で、通信経路断となった場合、OSPFで経路情報を更新しインターネット側のネットワークへ経路を切り替えます。それぞれの回線の通信ではIPsecでVPNを構築します。この例では、ルーターとして本製品をセンター側(ルーターA)、拠点側(ルーターB)に設置するネットワーク構成を例に解説します。
ISPからは次の情報を提供されているものとします。
| PPPユーザー名 | center@isp | branch@isp |
| PPPパスワード | centpass | brapass |
| PPPoEサービス名 | 指定なし | |
| IPアドレス | 200.100.10.1/32 | 動的割り当て |
| DNSサーバー | 接続時に通知される | |
| PPPユーザー名 | center | branch |
| PPPパスワード | passwdA | passwdB |
| PPPoEサービス名 | 指定なし | |
| 使用できるIPアドレス | 動的割り当て(172.16.0.1/32固定) | 動的割り当て(172.16.0.2/32固定) |
| 接続形態 | 端末型 | |
| WAN側物理インターフェース | gigabitEthernet 0 | gigabitEthernet 1 | gigabitEthernet 0 | gigabitEthernet 1 |
| WAN側IPアドレス | 172.16.0.1/32 | 200.100.10.1/32 | 172.16.0.2/32 | 動的割り当て |
| LAN側(vlan1)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 | ||
| VPN接続設定 | ||||
| ローカルセキュアグループ | 0.0.0.0/0 | 0.0.0.0/0 | 0.0.0.0/0 | 0.0.0.0/0 |
| リモートセキュアグループ | 0.0.0.0/0 | 0.0.0.0/0 | 0.0.0.0/0 | 0.0.0.0/0 |
| トンネル終端アドレス | 172.16.0.2/32 | 不定 | 172.16.0.1/32 | 200.100.10.1/32 |
| IKE設定 | ||||
| 交換モード | Mainモード | Aggressiveモード | Mainモード | Aggressiveモード |
| 認証方式 | 事前共有鍵(pre-shared key) | 事前共有鍵(pre-shared key) | ||
| 事前共有鍵 | secret(文字列) | secret(文字列) | ||
| ローカルID/リモートID | なし/なし | なし/client | なし/なし | client/なし |
| 暗号化認証アルゴリズム | 3DES & SHA1-DH2 | 3DES & SHA1-DH2 | ||
| 有効期限 | 21600秒 (6時間)(デフォルト) | 21600秒 (6時間)(デフォルト) | ||
| DPDによる死活監視 | 行う | 行う | ||
| 起動時のISAKMPネゴシエーション | 行う | 行わない | 行う | |
| IPsec設定 | ||||
| SAモード | トンネルモード | トンネルモード | ||
| セキュリティープロトコル | ESP | ESP | ||
| 暗号化認証アルゴリズム | 3DES & SHA1 | 3DES & SHA1 | ||
| PFSグループ | なし | なし | ||
| 有効期限 | 3600秒(1時間)(デフォルト) | 3600秒(1時間)(デフォルト) | ||

| ルーターAの設定 |
ppp profile pppoe0 ↓
my-username center password passwdA ↓
interface gigabitEthernet 0 ↓
no shutdown ↓
interface gigabitEthernet 0.1 ↓
ip address ipcp ↓
ip tcp mss auto ↓
no shutdown ↓
pppoe enable ↓
ppp bind-profile pppoe0 ↓
ip ids in protect ↓
ppp profile pppoe1 ↓
my-username center@isp password centpass ↓
interface gigabitEthernet 1 ↓
no shutdown ↓
interface gigabitEthernet 1.1 ↓
ip address 200.100.10.1/32 ↓
ip tcp mss auto ↓
no shutdown ↓
pppoe enable ↓
ppp bind-profile pppoe1 ↓
ip napt inside any ↓
ip ids in protect ↓
interface vlan 1 ↓
ip address 192.168.10.1/24 ↓
ip address-up-always ↓
ip route default gigabitEthernet 1.1 ↓
ip route 172.16.0.2/32 gigabitEthernet 0.1 ↓
ip route 172.16.0.2/32 Null 254 ↓
access-list ip extended pppoe0-in ↓
dynamic permit udp any interface gigabitEthernet 0.1 eq 500 ↓
access-list ip extended pppoe0-out ↓
dynamic permit ip any any ↓
interface gigabitEthernet 0.1 ↓
ip traffic-filter pppoe0-in in ↓
ip traffic-filter pppoe0-out out ↓
access-list ip extended pppoe1-in ↓
dynamic permit udp any interface gigabitEthernet 1.1 eq 500 ↓
access-list ip extended pppoe1-out ↓
dynamic permit ip any any ↓
interface gigabitEthernet 1.1 ↓
ip traffic-filter pppoe1-in in ↓
ip traffic-filter pppoe1-out out ↓
isakmp proposal isakmp encryption 3des hash sha1 group 2 ↓
isakmp policy vpn_1 ↓
peer 172.16.0.2 ↓
auth preshared key secret ↓
proposal isakmp ↓
keepalive enable ↓
isakmp policy vpn_2 ↓
peer any ↓
mode aggressive ↓
auth preshared key secret ↓
remote-id client ↓
proposal isakmp ↓
keepalive enable ↓
access-list ip extended ipsec ↓
permit ip any any ↓
ipsec proposal ipsec esp encryption 3des hash sha1 ↓
ipsec policy-name-link enable ↓
ipsec policy vpn_1 ↓
peer 172.16.0.2 ↓
access-list ipsec ↓
local-id 0.0.0.0/0 ↓
remote-id 0.0.0.0/0 ↓
proposal ipsec ↓
always-up-sa ↓
ipsec policy vpn_2 ↓
peer any ↓
access-list ipsec ↓
local-id 0.0.0.0/0 ↓
remote-id 0.0.0.0/0 ↓
proposal ipsec ↓
always-up-sa ↓
interface tunnel 0 ↓
tunnel mode ipsec ↓
ip unnumbered vlan 1 ↓
ip tcp mss auto ↓
no shutdown ↓
tunnel policy vpn_1 ↓
interface tunnel 1 ↓
tunnel mode ipsec ↓
ip unnumbered vlan 1 ↓
ip tcp mss auto ↓
no shutdown ↓
ip ospf cost 100 ↓
tunnel policy vpn_2 ↓
router ospf ↓
passive-interface vlan 1 ↓
network tunnel 0 area 0 ↓
network tunnel 1 area 0 ↓
network vlan 1 area 0 ↓
proxydns ip enable ↓
copy running-config startup-config ↓
| ルーターBの設定 |
ppp profile pppoe0 ↓
my-username branch password passwdB ↓
interface gigabitEthernet 0 ↓
no shutdown ↓
interface gigabitEthernet 0.1 ↓
ip address ipcp ↓
ip tcp mss auto ↓
no shutdown ↓
pppoe enable ↓
ppp bind-profile pppoe0 ↓
ip ids in protect ↓
ppp profile pppoe1 ↓
my-username branch@isp password brapass ↓
interface gigabitEthernet 1 ↓
no shutdown ↓
interface gigabitEthernet 1.1 ↓
ip address ipcp ↓
ip tcp mss auto ↓
no shutdown ↓
pppoe enable ↓
ppp bind-profile pppoe1 ↓
ip napt inside any ↓
ip ids in protect ↓
interface vlan 1 ↓
ip address 192.168.20.1/24 ↓
ip address-up-always ↓
ip route default gigabitEthernet 1.1 ↓
ip route 172.16.0.1/32 gigabitEthernet 0.1 ↓
ip route 172.16.0.1/32 Null 254 ↓
access-list ip extended pppoe0-in ↓
dynamic permit udp any interface gigabitEthernet 0.1 eq 500 ↓
access-list ip extended pppoe0-out ↓
dynamic permit ip any any ↓
interface gigabitEthernet 0.1 ↓
ip traffic-filter pppoe0-in in ↓
ip traffic-filter pppoe0-out out ↓
access-list ip extended pppoe1-in ↓
access-list ip extended pppoe1-out ↓
dynamic permit ip any any ↓
interface gigabitEthernet 1.1 ↓
ip traffic-filter pppoe1-in in ↓
ip traffic-filter pppoe1-out out ↓
isakmp proposal isakmp encryption 3des hash sha1 group 2 ↓
isakmp policy vpn_1 ↓
peer 172.16.0.1 ↓
auth preshared key secret ↓
proposal isakmp ↓
keepalive enable ↓
isakmp policy vpn_2 ↓
peer 200.100.10.1 ↓
mode aggressive ↓
auth preshared key secret ↓
local-id client ↓
proposal isakmp ↓
keepalive enable ↓
access-list ip extended ipsec ↓
permit ip any any ↓
ipsec proposal ipsec esp encryption 3des hash sha1 ↓
ipsec policy vpn_1 ↓
peer 172.16.0.1 ↓
access-list ipsec ↓
local-id 0.0.0.0/0 ↓
remote-id 0.0.0.0/0 ↓
proposal ipsec ↓
always-up-sa ↓
ipsec policy vpn_2 ↓
peer 200.100.10.1 ↓
access-list ipsec ↓
local-id 0.0.0.0/0 ↓
remote-id 0.0.0.0/0 ↓
proposal ipsec ↓
always-up-sa ↓
interface tunnel 0 ↓
tunnel mode ipsec ↓
ip unnumbered vlan 1 ↓
ip tcp mss auto ↓
no shutdown ↓
tunnel policy vpn_1 ↓
interface tunnel 1 ↓
tunnel mode ipsec ↓
ip unnumbered vlan 1 ↓
ip tcp mss auto ↓
no shutdown ↓
ip ospf cost 100 ↓
tunnel policy vpn_2 ↓
router ospf ↓
passive-interface vlan 1 ↓
network tunnel 0 area 0 ↓
network tunnel 1 area 0 ↓
network vlan 1 area 0 ↓
proxydns ip enable ↓
copy running-config startup-config ↓
| まとめ |
ルーターAのコンフィグ
! service password-encryption ! clock timezone JST 9 ! ! ! ! ip address-up-always ppp profile pppoe0 my-username center password 8 e$Ih7p7xgv6c0kA ppp profile pppoe1 my-username center@isp password 8 e$QrAq9z74BzW1jk1bEKE2+RAAA ! interface gigabitEthernet 0 no shutdown ! interface gigabitEthernet 0.1 ip address ipcp ip tcp mss auto no shutdown pppoe enable ppp bind-profile pppoe0 ip traffic-filter pppoe0-in in ip traffic-filter pppoe0-out out ip ids in protect ! interface gigabitEthernet 1 no shutdown ! interface gigabitEthernet 1.1 ip address 200.100.10.1/32 ip tcp mss auto no shutdown pppoe enable ppp bind-profile pppoe1 ip napt inside any ip traffic-filter pppoe1-in in ip traffic-filter pppoe1-out out ip ids in protect ! interface gigabitEthernet 2 no shutdown ! interface gigabitEthernet 3 no shutdown ! interface gigabitEthernet 4 no shutdown ! interface gigabitEthernet 5 no shutdown ! interface loop 0 shutdown ! interface loop 1 shutdown ! interface tunnel 0 tunnel mode ipsec ip unnumbered vlan 1 ip tcp mss auto no shutdown tunnel policy vpn_1 ! interface tunnel 1 tunnel mode ipsec ip unnumbered vlan 1 ip tcp mss auto no shutdown ip ospf cost 100 tunnel policy vpn_2 ! interface vlan 1 ip address 192.168.10.1/24 no shutdown ! router ospf passive-interface vlan 1 network tunnel 0 area 0 network tunnel 1 area 0 network vlan 1 area 0 ! ip route default gigabitEthernet 1.1 ip route 172.16.0.2/32 gigabitEthernet 0.1 ip route 172.16.0.2/32 Null 254 ! access-list ip extended ipsec permit ip any any access-list ip extended pppoe0-in dynamic permit udp any interface gigabitEthernet 0.1 eq 500 access-list ip extended pppoe0-out dynamic permit ip any any access-list ip extended pppoe1-in dynamic permit udp any interface gigabitEthernet 1.1 eq 500 access-list ip extended pppoe1-out dynamic permit ip any any ! isakmp proposal isakmp encryption 3des hash sha1 group 2 ! isakmp policy vpn_1 peer 172.16.0.2 auth preshared key 8 e$I3eQu7yNuLxQA proposal isakmp keepalive enable ! isakmp policy vpn_2 peer any mode aggressive auth preshared key 8 e$I3eQu7yNuLxQA remote-id client proposal isakmp keepalive enable ! ipsec proposal ipsec esp encryption 3des hash sha1 ! ipsec policy-name-link enable ! ipsec policy vpn_1 peer 172.16.0.2 access-list ipsec local-id 0.0.0.0/0 remote-id 0.0.0.0/0 proposal ipsec always-up-sa ! ipsec policy vpn_2 peer any access-list ipsec local-id 0.0.0.0/0 remote-id 0.0.0.0/0 proposal ipsec always-up-sa ! proxydns ip enable ! ! ! end |
ルーターBのコンフィグ
! service password-encryption ! clock timezone JST 9 ! ! ! ! ip address-up-always ppp profile pppoe0 my-username branch password 8 e$I6rT3jJQw6oIA ppp profile pppoe1 my-username branch@isp password 8 e$ILwks03RXPHAA ! interface gigabitEthernet 0 no shutdown ! interface gigabitEthernet 0.1 ip address ipcp ip tcp mss auto no shutdown pppoe enable ppp bind-profile pppoe0 ip traffic-filter pppoe0-in in ip traffic-filter pppoe0-out out ip ids in protect ! interface gigabitEthernet 1 no shutdown ! interface gigabitEthernet 1.1 ip address ipcp ip tcp mss auto no shutdown pppoe enable ppp bind-profile pppoe1 ip napt inside any ip traffic-filter pppoe1-in in ip traffic-filter pppoe1-out out ip ids in protect ! interface gigabitEthernet 2 no shutdown ! interface gigabitEthernet 3 no shutdown ! interface gigabitEthernet 4 no shutdown ! interface gigabitEthernet 5 no shutdown ! interface loop 0 shutdown ! interface loop 1 shutdown ! interface tunnel 0 tunnel mode ipsec ip unnumbered vlan 1 ip tcp mss auto no shutdown tunnel policy vpn_1 ! interface tunnel 1 tunnel mode ipsec ip unnumbered vlan 1 ip tcp mss auto no shutdown ip ospf cost 100 tunnel policy vpn_2 ! interface vlan 1 ip address 192.168.20.1/24 no shutdown ! router ospf passive-interface vlan 1 network tunnel 0 area 0 network tunnel 1 area 0 network vlan 1 area 0 ! ip route default gigabitEthernet 1.1 ip route 172.16.0.1/32 gigabitEthernet 0.1 ip route 172.16.0.1/32 Null 254 ! access-list ip extended ipsec permit ip any any access-list ip extended pppoe0-in dynamic permit udp any interface gigabitEthernet 0.1 eq 500 access-list ip extended pppoe0-out dynamic permit ip any any access-list ip extended pppoe1-in access-list ip extended pppoe1-out dynamic permit ip any any ! isakmp proposal isakmp encryption 3des hash sha1 group 2 ! isakmp policy vpn_1 peer 172.16.0.1 auth preshared key 8 e$I3eQu7yNuLxQA proposal isakmp keepalive enable ! isakmp policy vpn_2 peer 200.100.10.1 mode aggressive auth preshared key 8 e$I3eQu7yNuLxQA local-id client proposal isakmp keepalive enable ! ipsec proposal ipsec esp encryption 3des hash sha1 ! ipsec policy vpn_1 peer 172.16.0.1 access-list ipsec local-id 0.0.0.0/0 remote-id 0.0.0.0/0 proposal ipsec always-up-sa ! ipsec policy vpn_2 peer 200.100.10.1 access-list ipsec local-id 0.0.0.0/0 remote-id 0.0.0.0/0 proposal ipsec always-up-sa ! proxydns ip enable ! ! ! end |
(C) 2011-2014 アライドテレシスホールディングス株式会社
PN: 613-001568 Rev.E