[index] AT-NFV-APL Ver.1.8.1 リファレンスマニュアル

| ISP接続用ユーザー名 | user@ispA | user@ispB | |
| ISP接続用パスワード | isppasswdA | isppasswdB | |
| PPPoEサービス名 | 指定なし | 指定なし | |
| WAN側IPアドレス | 10.0.0.1/32 | 10.0.0.2/32 | |
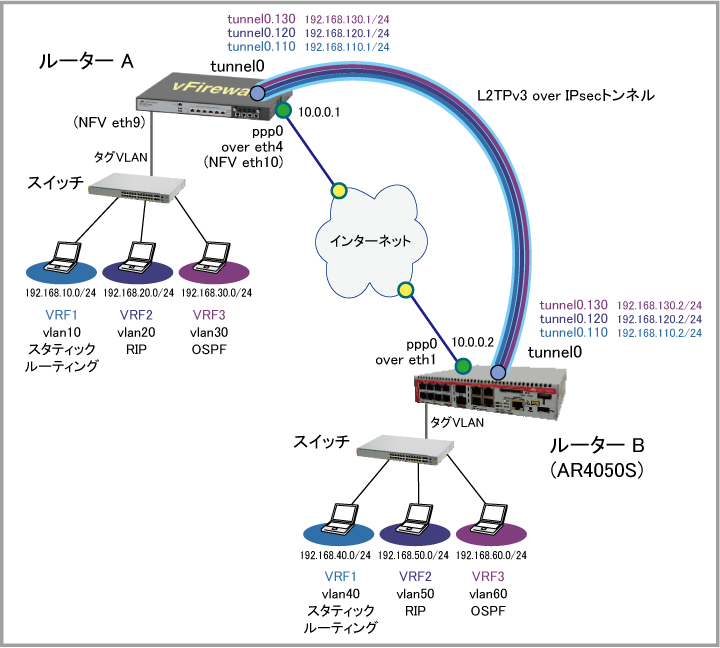
グローバルVRF |
WAN側(ISP)物理インターフェース(1) | eth4 (eth10) | eth1 |
| WAN側(ppp0)IPアドレス | 10.0.0.1/32 | 10.0.0.2/32 | |
| トンネルインターフェース | tunnel0 | tunnel0 | |
| トンネル終端IPアドレス | 10.0.0.1 | 10.0.0.2 | |
VRF1 |
LAN側インターフェース | eth1 (vlan10) | vlan40 |
| LAN側IPアドレス | 192.168.10.1/24 | 192.168.40.1/24 | |
| トンネルサブインターフェース | tunnel0.110 | tunnel0.110 | |
| トンネルサブインターフェースIPアドレス | 192.168.110.1/24 | 192.168.110.2/24 | |
VRF2 |
LAN側インターフェース | eth1 (vlan20) | vlan50 |
| LAN側IPアドレス | 192.168.20.1/24 | 192.168.50.1/24 | |
| トンネルサブインターフェース | tunnel0.120 | tunnel0.120 | |
| トンネルサブインターフェースIPアドレス | 192.168.120.1/24 | 192.168.120.2/24 | |
VRF3 |
LAN側インターフェース | eth1 (vlan30) | vlan60 |
| LAN側IPアドレス | 192.168.30.1/24 | 192.168.60.1/24 | |
| トンネルサブインターフェース | tunnel0.130 | tunnel0.130 | |
| トンネルサブインターフェースIPアドレス | 192.168.130.1/24 | 192.168.130.2/24 | |
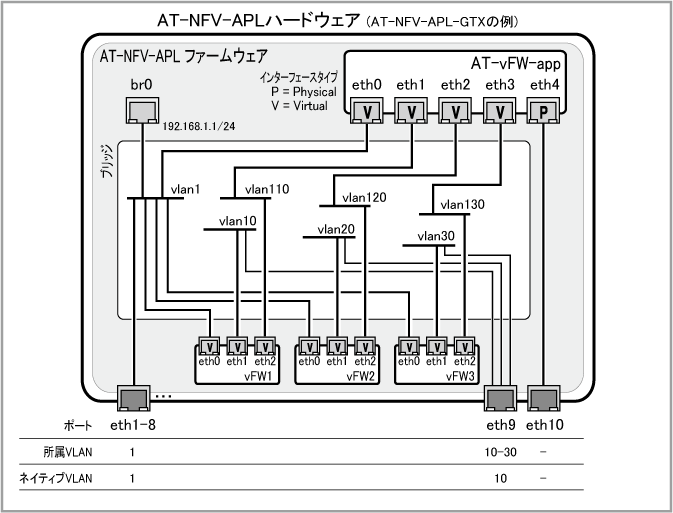
Note10ポート構成(eth1~eth10)のAT-NFV-APL-GTXを想定した例になっていますので、6ポート(eth1~eth6)構成のAT-NFV-APL-GTをご使用の場合は、使用するポートを適宜読み替えてください。
| br0 | 192.168.1.1/24 |
| eth1~eth8 | 1 | 1 |
| eth9 | 10-30 | 10 |
| eth10 | ||
インスタンス名 |
インターフェース名 |
タイプ |
VLAN ID |
インターフェース |
|
| AT-vFW-app | eth0 | Virtual | 1 | - | 192.168.1.2/24 |
| eth1 | Virtual | 110 | - | 未設定 | |
| eth2 | Virtual | 120 | - | 未設定 | |
| eth3 | Virtual | 130 | - | 未設定 | |
| eth4 | Physical | - | eth10 | 未設定 | |
| vFW1 | eth0 | Virtual | 1 | - | 192.168.1.3/24 |
| eth1 | Virtual | 10 | - | 192.168.10.1/24 | |
| eth2 | Virtual | 110 | - | 192.168.110.1/24 | |
| vFW2 | eth0 | Virtual | 1 | - | 192.168.1.4/24 |
| eth1 | Virtual | 20 | - | 192.168.20.1/24 | |
| eth2 | Virtual | 120 | - | 192.168.120.1/24 | |
| vFW3 | eth0 | Virtual | 1 | - | 192.168.1.5/24 |
| eth1 | Virtual | 30 | - | 192.168.30.1/24 | |
| eth2 | Virtual | 130 | - | 192.168.130.1/24 |
Note本例では各インスタンスのeth0インターフェースに管理用のIPアドレス(192.168.1.x/24)を設定しています。
管理用アドレスはインスタンス作成時に設定する必要がありますが、それ以外のIPアドレスはインスタンス作成時に設定しても、作成後に設定してもどちらでもかまいません。
interface eth4 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu
interface eth0 ip address 192.168.1.2/24
bridge 1 bridge 2 bridge 3
interface eth1 bridge-group 1
interface eth2 bridge-group 2
interface eth3 bridge-group 3
crypto isakmp key secret address 10.0.0.2
interface tunnel0 encapsulation dot1q 110 encapsulation dot1q 120 encapsulation dot1q 130 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.2 tunnel local id 1 tunnel remote id 2 tunnel protection ipsec tunnel mode l2tp v3 tunnel df clear
interface tunnel0.110 bridge-group 1 mtu 1500
interface tunnel0.120 bridge-group 2 mtu 1500
interface tunnel0.130 bridge-group 3 mtu 1500
ip route 0.0.0.0/0 ppp0
zone private network ctrl ip subnet 224.0.0.0/24 network lan ip subnet 192.168.0.0/16
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit any from public.wan.ppp0 to public rule 40 permit esp from public to public.wan.ppp0 rule 50 permit isakmp from public to public.wan.ppp0 rule 60 permit l2tp from public to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
end
interface eth0 ip address 192.168.1.3/24
interface eth1 ip address 192.168.10.1/24
interface eth2 ip address 192.168.110.1/24
ip route 192.168.40.0/24 192.168.110.2
end
interface eth0 ip address 192.168.1.4/24
interface eth1 ip address 192.168.20.1/24
interface eth2 ip address 192.168.120.1/24
router rip network 192.168.20.0/24 network 192.168.120.0/24 passive-interface eth0
end
interface eth0 ip address 192.168.1.5/24
interface eth1 ip address 192.168.30.1/24
interface eth2 ip address 192.168.130.1/24
router ospf passive-interface eth0 network 192.168.30.0/24 area 0.0.0.0 network 192.168.130.0/24 area 0.0.0.0
end
no spanning-tree rstp enable
interface eth1 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispB ppp password isppasswdB ip address 10.0.0.2/32 ip tcp adjust-mss pmtu
ip vrf VRF1 1
ip vrf VRF2 2
ip vrf VRF3 3
vlan database vlan 40,50,60 state enable
interface vlan40 ip vrf forwarding VRF1 ip address 192.168.40.1/24
interface vlan50 ip vrf forwarding VRF2 ip address 192.168.50.1/24
interface vlan60 ip vrf forwarding VRF3 ip address 192.168.60.1/24
interface port1.0.1 switchport mode trunk switchport trunk allowed vlan add 40,50,60 switchport trunk native vlan none
crypto isakmp key secret address 10.0.0.1
interface tunnel0 encapsulation dot1q 110 encapsulation dot1q 120 encapsulation dot1q 130 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local id 2 tunnel remote id 1 tunnel protection ipsec tunnel mode l2tp v3 tunnel df clear
interface tunnel0.110 mtu 1500 ip vrf forwarding VRF1 ip address 192.168.110.2/24 ip tcp adjust-mss pmtu
interface tunnel0.120 mtu 1500 ip vrf forwarding VRF2 ip address 192.168.120.2/24 ip tcp adjust-mss pmtu
interface tunnel0.130 mtu 1500 ip vrf forwarding VRF3 ip address 192.168.130.2/24 ip tcp adjust-mss pmtu
ip route 0.0.0.0/0 ppp0
ip route vrf VRF1 192.168.10.0/24 192.168.110.1
router rip address-family ipv4 vrf VRF2 network 192.168.0.0/16 exit-address-family
router ospf 3 VRF3 network 192.168.0.0 255.255.0.0 area 0
zone private network ctrl ip subnet 224.0.0.0/24 network lan ip subnet 192.168.0.0/16
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.2
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit any from public.wan.ppp0 to public rule 40 permit esp from public to public.wan.ppp0 rule 50 permit isakmp from public to public.wan.ppp0 rule 60 permit l2tp from public to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility local5 ↓
awplus# show log | include Firewall ↓
! interface eth4 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip address 10.0.0.1/32 ip tcp adjust-mss pmtu ! interface eth0 ip address 192.168.1.2/24 ! bridge 1 bridge 2 bridge 3 ! interface eth1 bridge-group 1 ! interface eth2 bridge-group 2 ! interface eth3 bridge-group 3 ! crypto isakmp key secret address 10.0.0.2 ! interface tunnel0 encapsulation dot1q 110 encapsulation dot1q 120 encapsulation dot1q 130 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.2 tunnel local id 1 tunnel remote id 2 tunnel protection ipsec tunnel mode l2tp v3 tunnel df clear ! interface tunnel0.110 bridge-group 1 mtu 1500 ! interface tunnel0.120 bridge-group 2 mtu 1500 ! interface tunnel0.130 bridge-group 3 mtu 1500 ! ip route 0.0.0.0/0 ppp0 ! zone private network ctrl ip subnet 224.0.0.0/24 network lan ip subnet 192.168.0.0/16 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit any from public.wan.ppp0 to public rule 40 permit esp from public to public.wan.ppp0 rule 50 permit isakmp from public to public.wan.ppp0 rule 60 permit l2tp from public to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! end
! interface eth0 ip address 192.168.1.3/24 ! interface eth1 ip address 192.168.10.1/24 ! interface eth2 ip address 192.168.110.1/24 ! ip route 192.168.40.0/24 192.168.110.2 ! end
! interface eth0 ip address 192.168.1.4/24 ! interface eth1 ip address 192.168.20.1/24 ! interface eth2 ip address 192.168.120.1/24 ! router rip network 192.168.20.0/24 network 192.168.120.0/24 passive-interface eth0 ! end
! interface eth0 ip address 192.168.1.5/24 ! interface eth1 ip address 192.168.30.1/24 ! interface eth2 ip address 192.168.130.1/24 ! router ospf passive-interface eth0 network 192.168.30.0/24 area 0.0.0.0 network 192.168.130.0/24 area 0.0.0.0 ! end
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispB ppp password isppasswdB ip address 10.0.0.2/32 ip tcp adjust-mss pmtu ! ip vrf VRF1 1 ! ip vrf VRF2 2 ! ip vrf VRF3 3 ! vlan database vlan 40,50,60 state enable ! interface vlan40 ip vrf forwarding VRF1 ip address 192.168.40.1/24 ! interface vlan50 ip vrf forwarding VRF2 ip address 192.168.50.1/24 ! interface vlan60 ip vrf forwarding VRF3 ip address 192.168.60.1/24 ! interface port1.0.1 switchport mode trunk switchport trunk allowed vlan add 40,50,60 switchport trunk native vlan none ! crypto isakmp key secret address 10.0.0.1 ! interface tunnel0 encapsulation dot1q 110 encapsulation dot1q 120 encapsulation dot1q 130 mtu 1500 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel local id 2 tunnel remote id 1 tunnel protection ipsec tunnel mode l2tp v3 tunnel df clear ! interface tunnel0.110 mtu 1500 ip vrf forwarding VRF1 ip address 192.168.110.2/24 ip tcp adjust-mss pmtu ! interface tunnel0.120 mtu 1500 ip vrf forwarding VRF2 ip address 192.168.120.2/24 ip tcp adjust-mss pmtu ! interface tunnel0.130 mtu 1500 ip vrf forwarding VRF3 ip address 192.168.130.2/24 ip tcp adjust-mss pmtu ! ip route 0.0.0.0/0 ppp0 ! ip route vrf VRF1 192.168.10.0/24 192.168.110.1 ! router rip address-family ipv4 vrf VRF2 network 192.168.0.0/16 exit-address-family ! router ospf 3 VRF3 network 192.168.0.0 255.255.0.0 area 0 ! zone private network ctrl ip subnet 224.0.0.0/24 network lan ip subnet 192.168.0.0/16 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.2 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit any from public.wan.ppp0 to public rule 40 permit esp from public to public.wan.ppp0 rule 50 permit isakmp from public to public.wan.ppp0 rule 60 permit l2tp from public to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! end
(C) 2021 - 2023 アライドテレシスホールディングス株式会社
PN: 613-002993 Rev.H