[index] AT-AR4000S-Cloud リファレンスマニュアル 5.5.3

(本製品) |
(AR4050S) |
|
| ISP接続用ユーザー名 | user@ispA | user@ispB |
| ISP接続用パスワード | isppasswdA | isppasswdB |
| PPPoEサービス名 | 指定なし | 指定なし |
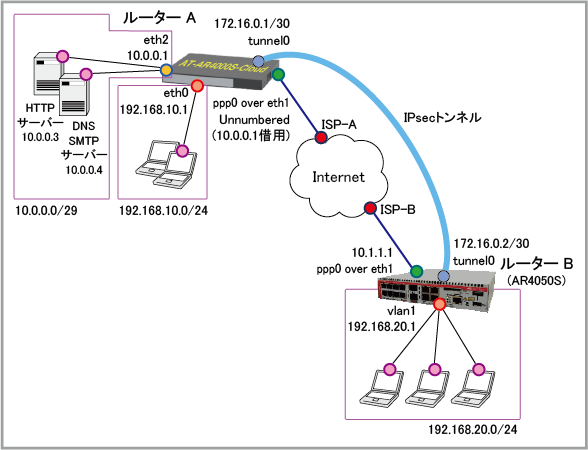
| 使用できるアドレス | 10.0.0.0/29 (10.0.0.0~10.0.0.7) |
10.1.1.1/32 |
| 接続形態 | LAN型(アドレス8個固定) | 端末型(アドレス1個固定) |
| WAN側物理インターフェース | eth1 | eth1 |
| WAN側(ppp0)IPアドレス | Unnumbered | 10.1.1.1/32 |
| DMZ側(eth2)IPアドレス | 10.0.0.1/29 | なし |
| LAN側(eth0/vlan1)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 |
| IKEバージョン・交換モード | ||
| アルゴリズム | ||
| アルゴリズム | ||
| eth0 | 192.168.10.1/24 | 管理用IPアドレス |
| eth1 | 未設定 | |
| eth2 | 未設定 |
Note構成が異なる場合はインターフェース名などを適宜読み替えてください。
interface eth1 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip unnumbered eth2 ip tcp adjust-mss pmtu
interface eth2 ip address 10.0.0.1/29
interface eth0 ip address 192.168.10.1/24
zone dmz network isp ip subnet 10.0.0.0/29 host dns-smtp ip address 10.0.0.4 host web ip address 10.0.0.3
zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit any from private to dmz rule 40 permit isakmp from public.wan.ppp0 to public rule 50 permit isakmp from public to public.wan.ppp0 rule 60 permit esp from public.wan.ppp0 to public rule 70 permit esp from public to public.wan.ppp0 rule 80 permit http from public to dmz.isp.web rule 90 permit dns from public to dmz.isp.dns-smtp rule 100 permit smtp from public to dmz.isp.dns-smtp protect
nat rule 10 masq any from private to public with src public.wan.ppp0 enable
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 version 1 mode main transform 1 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret address 10.1.1.1
crypto isakmp peer address 10.1.1.1 profile isakmp1
interface tunnel1 tunnel source eth2 tunnel destination 10.1.1.1 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 Null 254 ip route 192.168.20.0/24 tunnel1
end
no spanning-tree rstp enable
interface eth1 encapsulation ppp 0
interface ppp0 keepalive ppp username user@ispB ppp password isppasswdB ip address 10.1.1.1/32 ip tcp adjust-mss pmtu
interface vlan1 ip address 192.168.20.1/24
zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.1.1.1
application esp protocol 50
application isakmp protocol udp dport 500
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect
nat rule 10 masq any from private to public enable
crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 version 1 mode main transform 1 integrity SHA256 encryption AES128 group 15
crypto isakmp key secret address 10.0.0.1
crypto isakmp peer address 10.0.0.1 profile isakmp1
interface tunnel1 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 Null 254 ip route 192.168.10.0/24 tunnel1
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility local5 ↓
awplus# show log | include Firewall ↓
! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispA ppp password isppasswdA ip unnumbered eth2 ip tcp adjust-mss pmtu ! interface eth2 ip address 10.0.0.1/29 ! interface eth0 ip address 192.168.10.1/24 ! zone dmz network isp ip subnet 10.0.0.0/29 host dns-smtp ip address 10.0.0.4 host web ip address 10.0.0.3 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit any from private to dmz rule 40 permit isakmp from public.wan.ppp0 to public rule 50 permit isakmp from public to public.wan.ppp0 rule 60 permit esp from public.wan.ppp0 to public rule 70 permit esp from public to public.wan.ppp0 rule 80 permit http from public to dmz.isp.web rule 90 permit dns from public to dmz.isp.dns-smtp rule 100 permit smtp from public to dmz.isp.dns-smtp protect ! nat rule 10 masq any from private to public with src public.wan.ppp0 enable ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 version 1 mode main transform 1 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret address 10.1.1.1 ! crypto isakmp peer address 10.1.1.1 profile isakmp1 ! interface tunnel1 tunnel source eth2 tunnel destination 10.1.1.1 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.1/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 Null 254 ip route 192.168.20.0/24 tunnel1 ! end
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ppp username user@ispB ppp password isppasswdB ip address 10.1.1.1/32 ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.20.1/24 ! zone private network lan ip subnet 172.16.0.0/30 ip subnet 192.168.10.0/24 ip subnet 192.168.20.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.1.1.1 ! application esp protocol 50 ! application isakmp protocol udp dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public rule 40 permit isakmp from public to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public rule 60 permit esp from public to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! crypto ipsec profile ipsec1 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 version 1 mode main transform 1 integrity SHA256 encryption AES128 group 15 ! crypto isakmp key secret address 10.0.0.1 ! crypto isakmp peer address 10.0.0.1 profile isakmp1 ! interface tunnel1 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 172.16.0.2/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.10.0/24 Null 254 ip route 192.168.10.0/24 tunnel1 ! end
(C) 2022 - 2023 アライドテレシスホールディングス株式会社
PN: 613-003066 Rev.D