[index] AT-AR2050V/AT-AR3050S/AT-AR4050S コマンドリファレンス 5.4.6
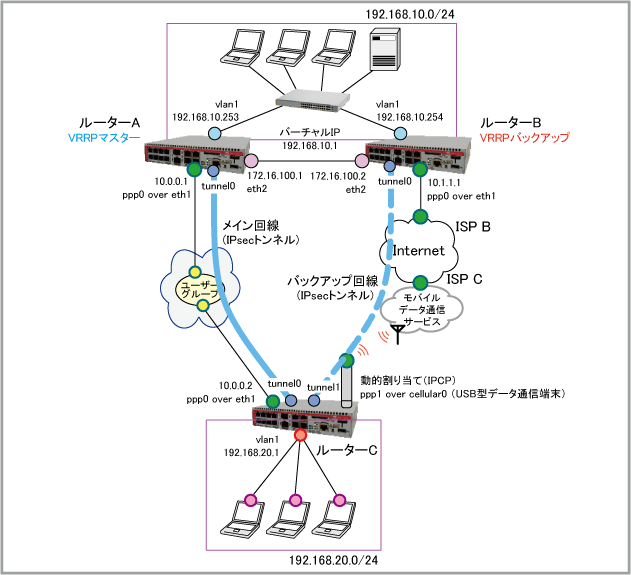
Note - 本設定例のルーターA、BはWANポートを2つ使用するため、AT-AR2050Vをこれらのルーターとして使用する場合は、eth2インターフェースをvlanインターフェースに変更してご使用ください。

| ISP接続用ユーザー名 | user@ispB | user@ispC | |
| ISP接続用パスワード | isppasswdB | isppasswdC | |
| アクセスポイント名(APN) | testname.alliedtelesis | ||
| WAN側IPアドレス | 10.1.1.1/32 | 動的割り当て(IPCP) | |
| CUG接続用ユーザー名 | userA@cug | userC@cug | |
| CUG接続用パスワード | cugpasswdA | cugpasswdC | |
| WAN側IPアドレス | 10.0.0.1/32 | 10.0.0.2/32 | |
| WAN側物理インターフェース(1) | eth1 | eth1 | eth1 |
| WAN側物理インターフェース(2) | cellular0(USB型データ通信端末) | ||
| WAN側(ppp0)IPアドレス(1) | 10.0.0.1/32 | 10.1.1.1/32 | 10.0.0.2/32 |
| WAN側(ppp1)IPアドレス(2) | 接続時にISPから取得 | ||
| LAN側(vlan1)IPアドレス | 192.168.10.253/24 | 192.168.10.254/24 | 192.168.20.1/24 |
| IPsecトンネル(tunnel0)IPアドレス(1) | 192.168.100.1/30 | 192.168.200.1/30 | 192.168.100.2/30 |
| IPsecトンネル(tunnel1)IPアドレス(2) | 192.168.200.2/30 | ||
no spanning-tree rstp enable |
interface eth1 encapsulation ppp 0 |
interface ppp0 keepalive ip address negotiated ppp username userA@cug ppp password cugpasswdA ip tcp adjust-mss pmtu |
interface eth2 ip address 172.16.100.1/24 |
interface vlan1 ip address 192.168.10.253/24 |
crypto isakmp key secret1 address 10.0.0.2 |
crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA1 encryption AES128 |
crypto isakmp profile isakmp1 version 1 mode main lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 |
crypto isakmp peer address 10.0.0.2 profile isakmp1 |
interface tunnel0 mtu 1300 tunnel source ppp0 tunnel destination 10.0.0.2 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.100.1/30 ip tcp adjust-mss 1260 |
router vrrp 1 vlan1 virtual-ip 192.168.10.1 backup priority 101 circuit-failover eth2 2 enable |
ping-poll 1 ip 10.0.0.2 normal-interval 10 up-count 5 sample-size 10 active |
trigger 1 type ping-poll 1 down script 1 flash:/pingdown.scp trigger 2 type ping-poll 1 up script 1 flash:/pingup.scp |
ip route 0.0.0.0/0 172.16.100.2 ip route 10.0.0.2/32 ppp0 ip route 10.0.0.2/32 Null 254 ip route 192.168.10.0/24 172.16.100.2 10 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 |
end |
no spanning-tree rstp enable |
interface eth1 encapsulation ppp 0 |
interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@ispB ppp password isppasswdB ip tcp adjust-mss pmtu |
interface eth2 ip address 172.16.100.2/24 |
interface vlan1 ip address 192.168.10.254/24 |
zone private network lan ip subnet 172.16.100.0/24 ip subnet 192.168.10.0/24 network peer ip subnet 192.168.20.0/24 network tunnel ip subnet 192.168.200.0/30 |
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.1.1.1 |
application esp protocol 50 |
application isakmp protocol udp sport 500 dport 500 |
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 protect |
nat rule 10 masq any from private to public enable |
crypto isakmp key secret2 hostname RouterC |
crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA1 encryption AES128 |
crypto isakmp profile isakmp1 version 1 mode aggressive lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 |
crypto isakmp peer dynamic profile isakmp1 |
interface tunnel0 mtu 1300 tunnel source ppp0 tunnel destination dynamic tunnel remote name RouterC tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.200.1/30 ip tcp adjust-mss 1260 |
router vrrp 1 vlan1 virtual-ip 192.168.10.1 backup enable |
ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 172.16.100.1 ip route 192.168.20.0/24 tunnel0 10 ip route 192.168.20.0/24 Null 254 |
end |
no spanning-tree rstp enable |
interface eth1 encapsulation ppp 0 |
interface ppp0 keepalive ip address negotiated ppp username userC@cug ppp password cugpasswdC ip tcp adjust-mss pmtu |
interface cellular0 encapsulation ppp 1 apn testname.alliedtelesis |
interface ppp1 keepalive ip address negotiated ppp username user@ispC ppp password isppasswdC ppp timeout idle 300 ip tcp adjust-mss pmtu |
interface vlan1 ip address 192.168.20.1/24 |
zone private network lan ip subnet 192.168.20.0/24 network peer ip subnet 0.0.0.0/0 interface tunnel0 ip subnet 0.0.0.0/0 interface tunnel1 ip subnet 192.168.10.0/24 |
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 ip subnet 0.0.0.0/0 interface ppp1 host ppp0 ip address 10.0.0.2 host ppp1 ip address dynamic interface ppp1 host RouterA ip address 10.0.0.1 |
application esp protocol 50 |
application isakmp protocol udp sport 500 dport 500 |
firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit isakmp from public.wan.ppp1 to public.wan rule 60 permit isakmp from public.wan to public.wan.ppp1 rule 70 permit esp from public.wan.ppp0 to public.wan rule 80 permit esp from public.wan to public.wan.ppp0 rule 90 permit esp from public.wan.ppp1 to public.wan rule 100 permit esp from public.wan to public.wan.ppp1 rule 110 permit ping from public.wan.ppp0 to public.wan.RouterA rule 120 permit ping from public.wan.RouterA to public.wan.ppp0 protect |
crypto isakmp key secret1 address 10.0.0.1 crypto isakmp key secret2 address 10.1.1.1 |
crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA1 encryption AES128 |
crypto isakmp profile isakmp1 version 1 mode main lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 |
crypto isakmp profile isakmp2 version 1 mode aggressive lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 |
crypto isakmp peer address 10.0.0.1 profile isakmp1 crypto isakmp peer address 10.1.1.1 profile isakmp2 |
interface tunnel0 mtu 1300 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.100.2/30 ip tcp adjust-mss 1260 |
interface tunnel1 mtu 1300 tunnel source ppp1 tunnel destination 10.1.1.1 tunnel local name RouterC tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.200.2/30 ip tcp adjust-mss 1260 |
ping-poll 1 ip 172.16.100.2 source-ip 192.168.20.1 normal-interval 10 up-count 5 sample-size 10 active |
ping-poll 2 ip 172.16.100.1 source-ip 192.168.20.1 normal-interval 10 up-count 5 sample-size 10 |
trigger 1 type ping-poll 1 down script 1 flash:/pingdown.scp trigger 2 type ping-poll 2 up script 1 flash:/pingup.scp |
ip route 0.0.0.0/0 tunnel0 ip route 10.0.0.1/32 ppp0 ip route 10.0.0.1/32 Null 254 ip route 10.1.1.1/32 Null 254 |
end |
awplus# copy running-config startup-config ↓ Building configuration... [OK] |
awplus# write memory ↓ Building configuration... [OK] |
awplus(config)# log buffered level informational program kernel msgtext Firewall ↓ |
awplus# show log | include firewall ↓ |
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ip address negotiated ppp username userA@cug ppp password cugpasswdA ip tcp adjust-mss pmtu ! interface eth2 ip address 172.16.100.1/24 ! interface vlan1 ip address 192.168.10.253/24 ! crypto isakmp key secret1 address 10.0.0.2 ! crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA1 encryption AES128 ! crypto isakmp profile isakmp1 version 1 mode main lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 ! crypto isakmp peer address 10.0.0.2 profile isakmp1 ! interface tunnel0 mtu 1300 tunnel source ppp0 tunnel destination 10.0.0.2 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.100.1/30 ip tcp adjust-mss 1260 ! router vrrp 1 vlan1 virtual-ip 192.168.10.1 backup priority 101 circuit-failover eth2 2 enable ! ping-poll 1 ip 10.0.0.2 normal-interval 10 up-count 5 sample-size 10 active ! trigger 1 type ping-poll 1 down script 1 flash:/pingdown.scp trigger 2 type ping-poll 1 up script 1 flash:/pingup.scp ! ip route 0.0.0.0/0 172.16.100.2 ip route 10.0.0.2/32 ppp0 ip route 10.0.0.2/32 Null 254 ip route 192.168.10.0/24 172.16.100.2 10 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 ! end |
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 ppp ipcp dns request keepalive ip address negotiated ppp username user@ispB ppp password isppasswdB ip tcp adjust-mss pmtu ! interface eth2 ip address 172.16.100.2/24 ! interface vlan1 ip address 192.168.10.254/24 ! zone private network lan ip subnet 172.16.100.0/24 ip subnet 192.168.10.0/24 network peer ip subnet 192.168.20.0/24 network tunnel ip subnet 192.168.200.0/30 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.1.1.1 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit esp from public.wan.ppp0 to public.wan rule 60 permit esp from public.wan to public.wan.ppp0 protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret2 hostname RouterC ! crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA1 encryption AES128 ! crypto isakmp profile isakmp1 version 1 mode aggressive lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 ! crypto isakmp peer dynamic profile isakmp1 ! interface tunnel0 mtu 1300 tunnel source ppp0 tunnel destination dynamic tunnel remote name RouterC tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.200.1/30 ip tcp adjust-mss 1260 ! router vrrp 1 vlan1 virtual-ip 192.168.10.1 backup enable ! ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 172.16.100.1 ip route 192.168.20.0/24 tunnel0 10 ip route 192.168.20.0/24 Null 254 ! end |
! no spanning-tree rstp enable ! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ip address negotiated ppp username userC@cug ppp password cugpasswdC ip tcp adjust-mss pmtu ! interface cellular0 encapsulation ppp 1 apn testname.alliedtelesis ! interface ppp1 keepalive ip address negotiated ppp username user@ispC ppp password isppasswdC ppp timeout idle 300 ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.20.1/24 ! zone private network lan ip subnet 192.168.20.0/24 network peer ip subnet 0.0.0.0/0 interface tunnel0 ip subnet 0.0.0.0/0 interface tunnel1 ip subnet 192.168.10.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 ip subnet 0.0.0.0/0 interface ppp1 host ppp0 ip address 10.0.0.2 host ppp1 ip address dynamic interface ppp1 host RouterA ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit isakmp from public.wan.ppp1 to public.wan rule 60 permit isakmp from public.wan to public.wan.ppp1 rule 70 permit esp from public.wan.ppp0 to public.wan rule 80 permit esp from public.wan to public.wan.ppp0 rule 90 permit esp from public.wan.ppp1 to public.wan rule 100 permit esp from public.wan to public.wan.ppp1 rule 110 permit ping from public.wan.ppp0 to public.wan.RouterA rule 120 permit ping from public.wan.RouterA to public.wan.ppp0 protect ! crypto isakmp key secret1 address 10.0.0.1 crypto isakmp key secret2 address 10.1.1.1 ! crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA1 encryption AES128 ! crypto isakmp profile isakmp1 version 1 mode main lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 ! crypto isakmp profile isakmp2 version 1 mode aggressive lifetime 3600 transform 1 integrity SHA1 encryption AES128 group 2 ! crypto isakmp peer address 10.0.0.1 profile isakmp1 crypto isakmp peer address 10.1.1.1 profile isakmp2 ! interface tunnel0 mtu 1300 tunnel source ppp0 tunnel destination 10.0.0.1 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.100.2/30 ip tcp adjust-mss 1260 ! interface tunnel1 mtu 1300 tunnel source ppp1 tunnel destination 10.1.1.1 tunnel local name RouterC tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.200.2/30 ip tcp adjust-mss 1260 ! ping-poll 1 ip 172.16.100.2 source-ip 192.168.20.1 normal-interval 10 up-count 5 sample-size 10 active ! ping-poll 2 ip 172.16.100.1 source-ip 192.168.20.1 normal-interval 10 up-count 5 sample-size 10 ! trigger 1 type ping-poll 1 down script 1 flash:/pingdown.scp trigger 2 type ping-poll 2 up script 1 flash:/pingup.scp ! ip route 0.0.0.0/0 tunnel0 ip route 10.0.0.1/32 ppp0 ip route 10.0.0.1/32 Null 254 ip route 10.1.1.1/32 Null 254 ! end |
enable clear isakmp sa configure terminal interface eth2 shutdown end |
enable configure terminal interface eth2 no shutdown end |
enable configure terminal no ip route 0.0.0.0/0 tunnel0 ip route 10.1.1.1/32 ppp1 ip rou 0.0.0.0/0 tunnel1 ping-poll 2 active exit ping-poll 1 no active end clear isakmp sa |
enable configure terminal ip route 0.0.0.0/0 tunnel0 no ip route 10.1.1.1/32 ppp1 no ip rou 0.0.0.0/0 tunnel1 ping-poll 1 active ping-poll 2 no active end clear isakmp sa |
(C) 2015 - 2016 アライドテレシスホールディングス株式会社
PN: 613-002107 Rev.K