[index] AT-AR1050V コマンドリファレンス 5.5.4
Note本設定例は、IKEv1を利用したIPsec VPNの一構成例であり、Juniper SRXシリーズとの接続性を保証するものではありません。
Note以下に述べる手順は一例です。使用するファームウェアのバージョンなどによっては、以下の手順で接続できない可能性もあります。詳しくは、各製品のマニュアルなどをご参照ください。

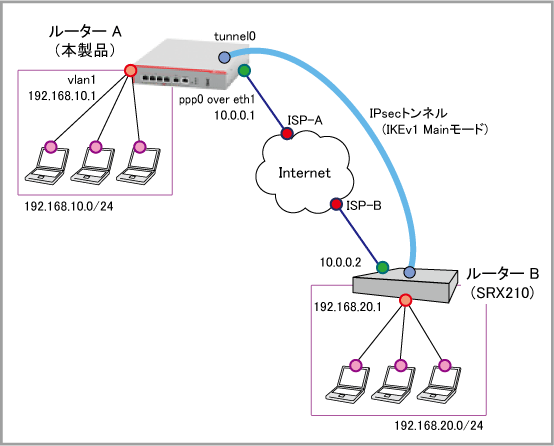
(本製品) |
(SRX210) |
|
| ISP接続用ユーザー名 | user@isp1 | user@isp2 |
| ISP接続用パスワード | isppasswd1 | isppasswd2 |
| PPPoEサービス名 | 指定なし | 指定なし |
| WAN側IPアドレス | 10.0.0.1/32 | 10.0.0.2/32 |
| WAN側物理インターフェース | eth1 | ge-0/0/0 |
| WAN側(ppp0)IPアドレス | 10.0.0.1/32 | 10.0.0.2/32 |
| LAN側(vlan1)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 |
| ローカルセレクター | 192.168.10.0/24 | 192.168.20.0/24 |
| リモートセレクター | 192.168.20.0/24 | 192.168.10.0/24 |
| IKEバージョン・交換モード | ||
| アルゴリズム | ||
| ローカルID | 始点アドレス(デフォルト) | 始点アドレス |
| SA有効期間 | ||
| アルゴリズム | ||
interface eth1 encapsulation ppp 0
interface ppp0 keepalive ip address 10.0.0.1/32 ppp username user@isp1 ppp password isppasswd1 ip tcp adjust-mss pmtu
interface vlan1 ip address 192.168.10.1/24
zone private network lan ip subnet 192.168.10.0/24 network peer ip subnet 192.168.20.0/24 interface tunnel0 network tunnel ip subnet 192.168.100.0/30
zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1
application esp protocol 50
application isakmp protocol udp sport 500 dport 500
firewall rule 10 permit esp from public.wan.ppp0 to public.wan rule 20 permit esp from public.wan to public.wan.ppp0 rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit any from private to private rule 60 permit any from private to public protect
nat rule 10 masq any from private to public enable
crypto isakmp key secret address 10.0.0.2
crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA256 encryption AES128
crypto isakmp profile isakmp1 version 1 mode main lifetime 3600 transform 1 integrity SHA256 encryption AES128 group 2
crypto isakmp peer address 10.0.0.2 profile isakmp1
interface tunnel0 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel local selector 192.168.10.0/24 tunnel remote selector 192.168.20.0/24 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.100.1/30 ip tcp adjust-mss 1260 mtu 1300
ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254
end
copy running-config startup-config」の書式で実行します。awplus# copy running-config startup-config ↓ Building configuration... [OK]
awplus# write memory ↓ Building configuration... [OK]
awplus(config)# log buffered level informational facility local5 ↓
awplus# show log | include Firewall ↓
NoteSRX210の設定に関する詳細は、SRX210のドキュメントをご参照ください。
delete
set system root-authentication encrypted-password New password: PasswordS Retype new password: PasswordS
set interfaces ge-0/0/1 unit 0 family inet address 192.168.20.1/24
set interfaces ge-0/0/0 unit 0 encapsulation ppp-over-ether set interfaces pp0 unit 0 ppp-options chap default-chap-secret "isppasswd2" set interfaces pp0 unit 0 ppp-options chap local-name "user@isp2" set interfaces pp0 unit 0 ppp-options chap passive set interfaces pp0 unit 0 pppoe-options underlying-interface ge-0/0/0.0 set interfaces pp0 unit 0 pppoe-options auto-reconnect 10 set interfaces pp0 unit 0 pppoe-options client set interfaces pp0 unit 0 family inet negotiate-address
set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone untrust interfaces pp0.0 host-inbound-traffic system-services ike set security zones security-zone untrust interfaces pp0.0 host-inbound-traffic system-services ping set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/1.0
set security nat source rule-set TrustToUntrust from zone trust set security nat source rule-set TrustToUntrust to zone untrust set security nat source rule-set TrustToUntrust rule match1 match source-address 0.0.0.0/0 set security nat source rule-set TrustToUntrust rule match1 then source-nat interface
set security zones security-zone vpn_zone address-book address net1 192.168.10.0/16 set security zones security-zone trust address-book address net2 192.168.20.0/24
set interfaces st0 unit 0 family inet set security zones security-zone vpn_zone interfaces st0.0
set security ike respond-bad-spi 5 set security ike proposal ar-p1 authentication-method pre-shared-keys set security ike proposal ar-p1 dh-group group2 set security ike proposal ar-p1 authentication-algorithm sha-256 set security ike proposal ar-p1 encryption-algorithm aes-128-cbc set security ike proposal ar-p1 lifetime-seconds 3600 set security ike policy p1-policy mode main set security ike policy p1-policy proposals ar-p1 set security ike policy p1-policy pre-shared-key ascii-text "secret" set security ike gateway ar-gw ike-policy p1-policy set security ike gateway ar-gw address 10.0.0.1 set security ike gateway ar-gw dead-peer-detection always-send set security ike gateway ar-gw dead-peer-detection interval 20 set security ike gateway ar-gw dead-peer-detection threshold 5 set security ike gateway ar-gw external-interface pp0.0
set security ipsec proposal ar-p2 protocol esp set security ipsec proposal ar-p2 authentication-algorithm hmac-sha256-128 set security ipsec proposal ar-p2 encryption-algorithm aes-128-cbc set security ipsec proposal ar-p2 lifetime-seconds 3600 set security ipsec policy p2-policy proposals ar-p2 set security ipsec vpn ar-vpn bind-interface st0.0 set security ipsec vpn ar-vpn ike gateway ar-gw set security ipsec vpn ar-vpn ike proxy-identity local 192.168.20.0/24 set security ipsec vpn ar-vpn ike proxy-identity remote 192.168.10.0/24 set security ipsec vpn ar-vpn ike proxy-identity service any set security ipsec vpn ar-vpn ike ipsec-policy p2-policy set security ipsec vpn ar-vpn establish-tunnels immediately set security flow tcp-mss ipsec-vpn mss 1300
set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit set security policies from-zone trust to-zone vpn_zone policy trust-to-vpn_zone match source-address net2 set security policies from-zone trust to-zone vpn_zone policy trust-to-vpn_zone match destination-address net1 set security policies from-zone trust to-zone vpn_zone policy trust-to-vpn_zone match application any set security policies from-zone trust to-zone vpn_zone policy trust-to-vpn_zone then permit set security policies from-zone vpn_zone to-zone trust policy vpn_zone-to-trust match source-address net1 set security policies from-zone vpn_zone to-zone trust policy vpn_zone-to-trust match destination-address net2 set security policies from-zone vpn_zone to-zone trust policy vpn_zone-to-trust match application any set security policies from-zone vpn_zone to-zone trust policy vpn_zone-to-trust then permit
set routing-options static route 0.0.0.0/0 next-hop pp0.0 set routing-options static route 192.168.10.0/24 next-hop st0.0
commit
! interface eth1 encapsulation ppp 0 ! interface ppp0 keepalive ip address 10.0.0.1/32 ppp username user@isp1 ppp password isppasswd1 ip tcp adjust-mss pmtu ! interface vlan1 ip address 192.168.10.1/24 ! zone private network lan ip subnet 192.168.10.0/24 network peer ip subnet 192.168.20.0/24 interface tunnel0 network tunnel ip subnet 192.168.100.0/30 ! zone public network wan ip subnet 0.0.0.0/0 interface ppp0 host ppp0 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit esp from public.wan.ppp0 to public.wan rule 20 permit esp from public.wan to public.wan.ppp0 rule 30 permit isakmp from public.wan.ppp0 to public.wan rule 40 permit isakmp from public.wan to public.wan.ppp0 rule 50 permit any from private to private rule 60 permit any from private to public protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret address 10.0.0.2 ! crypto ipsec profile ipsec1 lifetime seconds 3600 transform 1 protocol esp integrity SHA256 encryption AES128 ! crypto isakmp profile isakmp1 version 1 mode main lifetime 3600 transform 1 integrity SHA256 encryption AES128 group 2 ! crypto isakmp peer address 10.0.0.2 profile isakmp1 ! interface tunnel0 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel local selector 192.168.10.0/24 tunnel remote selector 192.168.20.0/24 tunnel protection ipsec profile ipsec1 tunnel mode ipsec ipv4 ip address 192.168.100.1/30 ip tcp adjust-mss 1260 mtu 1300 ! ip route 0.0.0.0/0 ppp0 ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 Null 254 ! end
(本製品) |
(SRX210) |
|
| ISP接続用ユーザー名 | user@isp1 | user@isp2 |
| ISP接続用パスワード | isppasswd1 | isppasswd2 |
| PPPoEサービス名 | 指定なし | 指定なし |
| WAN側IPアドレス | 動的割り当て(IPCP) | 10.0.0.2/32 |
| WAN側物理インターフェース | eth1 | ge-0/0/0 |
| WAN側(ppp0)IPアドレス | 接続時にISPから取得 | 10.0.0.2/32 |
| LAN側(vlan1)IPアドレス | 192.168.10.1/24 | 192.168.20.1/24 |
| ローカルセレクター | 192.168.10.0/24 | 192.168.20.0/24 |
| リモートセレクター | 192.168.20.0/24 | 192.168.10.0/24 |
| IKEバージョン・交換モード | ||
| アルゴリズム | ||
| ローカルID | client | 始点アドレス |
| SA有効期間 | ||
| アルゴリズム | ||
crypto isakmp profile isakmp1 version 1 mode aggressive lifetime 3600 transform 1 integrity SHA256 encryption AES128 group 2
interface tunnel0 tunnel source ppp0 tunnel local name client
set security ike policy p1-policy mode aggressive
set security ike gateway ar-gw dynamic hostname client
(C) 2019 - 2024 アライドテレシスホールディングス株式会社
PN: 613-002735 Rev.AD